Here is a piece by Robert Richardson from the CSI Blog . He discusses what one of his colleages calls “some of the weaknesses or downright drawbracks of strong authentication methods”:
There's this author named Kathy Siena who's currently at the center of one of those firestorms that break out on the Web now and again. Some threatening material regarding her was posted on the Web, she blames some fairly prominent bloggers of being involved in one way or another, and the rest seems to be finger pointing and confusion.
One detail of the saga worth considering is that one of the implicated bloggers claims that actions were taken by someone using his identity and access to his passworded accounts (this is quoted from Kim Cameron's Blog):
I am writing this from a new computer, using an email address that will be deleted at the end of this.I am no longer me. My main machine despite my best efforts has been hacked, my accounts compromised including my email. and has been disconnected from the internet.
How did this happen? When did this happen?
This is, to be sure, something of doomsday scenario for an individual user–the complete breach of one's identity across all the systems one uses and cares about (I'm assuming that the person in question, Allen Harrell, is telling the truth about being hacked).
Kim Cameron writes this on his blog:
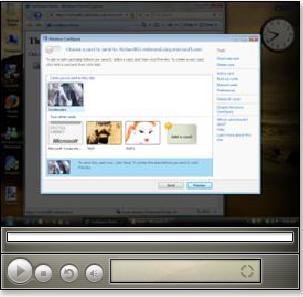
Maybe next time Allan and colleagues will be using Information Cards, not passwords, not shared secrets. This won’t extinguish either flaming or trolling, but it can sure make breaking in to someone’s site unbelievably harder – assuming we get to the point where our blogging software is safe too.
But I'm not convinced of this for a couple of reasons. First, Information Cards may or may not make breaking into someone's site unbelievably harder. Hackers sidestep the authentication process (strong or otherwise) all the time. Second, the perception of super-duper strong identity management may make it harder to prove that one's identity was in fact hacked.
InfoCard credentials are only more reliable if the system where they are being used is highly secure. If I'm using a given highly trusted credential from my system, but my system has been compromised, then the situation just looks worse for me when people start accusing me of misdeeds that were carried out in my name.
Many discussions about better credentialing begin from an underlying presumption that there will be a more secure operating system providing protection to the credentials and the subsystem that manages them. But at present, no one can point to that operating system. It certainly isn't Vista, however much improved its security may be.
Designing for Breach
I agree with Robert that credentials are only part of the story. That's why I said, “assuming we get to the point where our blogging software is safe too.”
Maybe that sounds simplistic. What did I mean by “safe”?
I'll start by saying I don't believe the idea of an unbreachable system is a useful operational concept. If we were to produce such a system, we wouldn't know it. The mere fact that a system hasn't been breached, or that we don't know how it could be, doesn't mean that a breach is not possible. The only systems we can build are those that “might” be breached.
The way to design securely is to assume your system WILL be breached and create a design that mitigates potential damage. There is nothing new in this – it is just risk management applied to security.
As a consequence, each component of the system must be isolated – to the extent possible – in an attempt to prevent contagion from compromised pieces.
Security Binarism versus Probabilities
I know Robert will agree with me that one of the things we have to avoid at all costs is “security binarism”. In this view, either something is secure or it isn't secure. If its adherants can find any potential vulnerability in something, they conclude the whole thing is vulnerable, so we might as well give up trying to protect it. Of course this isn't the way reality works – or the way anything real can be secured.
Let's use the analogy of physical security. I'll conjure up our old friend, the problem of protecting a castle.
You want a good outer wall – the higher and thicker the better. Then you want a deep moat – full of alligators and poisonous snakes. Why? If someone gets over the wall, you want them to have to cross the moat. If they don't drown in the moat, you want them to be eaten or bitten (those were the days!) And after the moat, you would have another wall, with places to launch boiling oil, shoot arrows, and all the rest. I could go on, but will spare you the obviousness of the excercise.
The point is, someone can breach the moat, but will then hit the next barrier. It doesn't take a deep grasp of statistics to see that if there is a probability of breach associated with each of these components, the probability of breaking through to the castle keep is the product of all the probabilities. So if you have five barriers, then even if each has a very high probability of breach (say 10%), the overall probability of breaking through all the barriers is just .001%. This is what lies behind the extreme power of combining numerous defences – especially if breaking through each defence requires completely unrelated skills and resources.
But despite the best castle design, we all know that the conquering hero can still dress up as a priest and walk in through the drawbridge without being detected (I saw the movie). In other words, there is a social engineering attack.
So, CardSpace may be nothing more than a really excellent moat. There may be other ways into the castle. But having a really great moat is in itself a significant advance in terms of “defence in depth”.
Beyond that, Information Cards begin to frame many questions better than they have been framed in the past – questions like, “Why am I retaining data that creates potential liability?”
In terms of Robert's fear that strong authentication will lead to hallucinations of non-repudiation, I agree that this is a huge potential problem. We need to start thinking about it and planning for it now. CSI can play an important role in educating professionals, government and citizens about these issues.
I recently expanded on these ideas here.

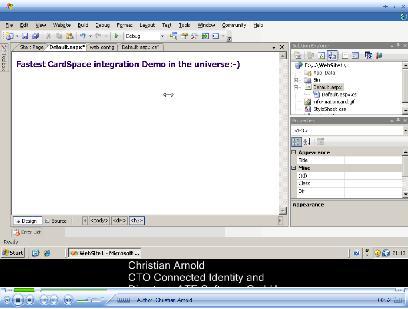

 The coolest thing in the session was the first public demo of the Bandit/Higgins cross-platform Identity Selector. During the demo Dale and I both used the same self-issued Information Card (that I created on the BrainShare show floor 🙂 ) to log into a Bandit relying party site, Dale from Linux and me with Windows CardSpace. As Dale and
The coolest thing in the session was the first public demo of the Bandit/Higgins cross-platform Identity Selector. During the demo Dale and I both used the same self-issued Information Card (that I created on the BrainShare show floor 🙂 ) to log into a Bandit relying party site, Dale from Linux and me with Windows CardSpace. As Dale and