Microsoft is Finally Being Relevant
Surprise surprise. For the last few years it looked as if the battling business units and power struggles within Microsoft had all but rendered the company incapable of doing anything innovative or relevant. But clearly something has happened to change this lack of leadership and apparent stumbling in the dark. Microsoft is not only doing something innovative — but profoundly innovative.
In a dual post by Microsoft’s John Shewchuk and Kim Cameron, the announcement was made about what Kim Cameron alluded to at the KuppingerCole EIC in April — Identity Management as a Service (IDMaaS). This is not trivial, and does not suck. It ROCKS.
Why is Identity Management as a Service a Big Deal
From a technical perspective, the place where innovation really makes a difference is the place where the rubber meets the road — infrastructure. Infrastructure is not only fundamental—as it provides the technical framework and underpinning to support big change — but infrastructure is hard.
It’s also hard to get funded and hard to sell both outside and inside of companies that make infrastructure.
This is because there is little possibility of showing a direct ROI in core infrastructure investment. It takes vision and guts to invest in infrastructure.
Nobody wants to buy identity infrastructure. In fact no one should have to pay for identity infrastructure. It should be ubiquitous, work, and be free to everyone and controlled by no one. Infrastructure at this level is as fundamental as air. You don’t think about it, you don’t buy it; you just breathe it in and out and get on with the details.
Metaphorically, when it comes to the maturity of identity infrastructure today—we are all sucking on thin air from teeny tubes of infrastructure veneer connected to identity silos (Facebook Connect, Twitter, Federated Identity and so on.)
It’s much like the other core suite of protocols of the Internet — like TCP/IP. TCP/IP is free as far as a piece of software goes. No one ever pays for the transport anymore.
So should be the protocols and infrastructure for doing Identity Management. With this announcement Microsoft is showing that it understands Identity Infrastructure is fundamental to everything in the hybrid world of social-mobile-cloud networking that we are stumbling towards.
Further, Microsoft is making it clear it understands that the current identity provider-centric world we live in now is broken and simply will not work for the future. Significant movement forward from this wretched state requires massive change — which is what Microsoft is proposing.
From a political and business perspective, Kim Cameron’s vision of a ubiquitous Identity Metasystem has somehow prevailed inside Microsoft and is starting to emerge. This is a big deal. Finally a company with lots of talent that has been wallowing from lack of leadership has stepped up and put a stake in the ground about Identity. Bravo!
Everybody else of significance that could be doing something significant with identity infrastructure — Google, Facebook, and Amazon for starters — are trapped in their current business models of trafficking your identity for short term profit. For each of them, the little piece they hold captive of your identity is the product by which they are making money. This is both short sighted and unsustainable.
Microsoft’s plan is much grander. Invest in the hard stuff, solve the really tough identity infrastructure problems across the board—simple, private, and scalable. By taking this high road, Microsoft is betting it can take the leadership role by increasing the size of the pie for other SaaS services and apps that organizations and individuals want and are willing to pay for. Much more visionary that continuing to fight over whatever crumb you can get based on the current broken model.
If Microsoft is allowed to pull this off, it is a good thing.
Stop Gushing and Lay it Out for Me
To understand the significance of IDMaaS, it’s useful to take a quick look at how identity management systems have evolved.
Figure 1 shows how identities started out being managed within the boundaries of a domain. Domain-based identity managed need hardly be mentioned here as it can’t possibly meet any of the requirements for identity management in today’s organizational environments. For its day, it worked and it was a good place to start.
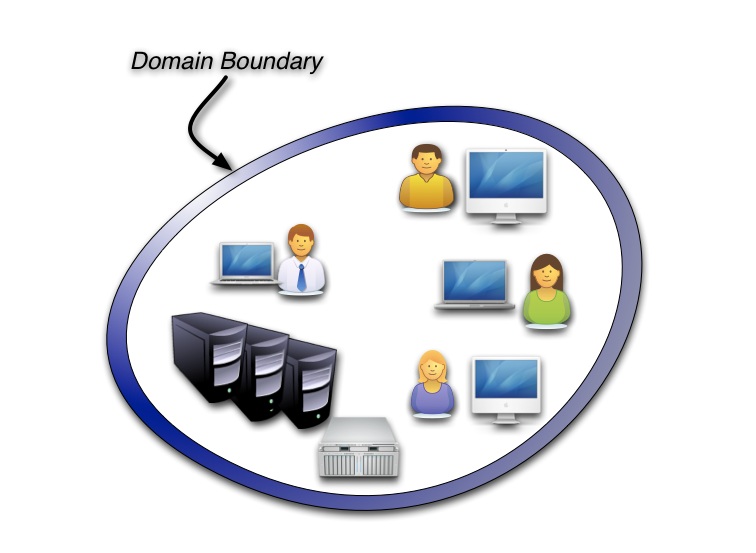
Figure 1: Domain Contained Identity
Figure 2 illustrates the first generation of federated identity management systems. This is a powerful model and was a big step forward from the domain model. In this model there is a service provider that accepts claims from an identity provider. A person can then prove who they are to the identity provider and present claims to the service provider to assure proper access to services and resources. This model works when these a relatively small number of parties involved. But as soon as there a diverse number of parties, it quickly breaks down.
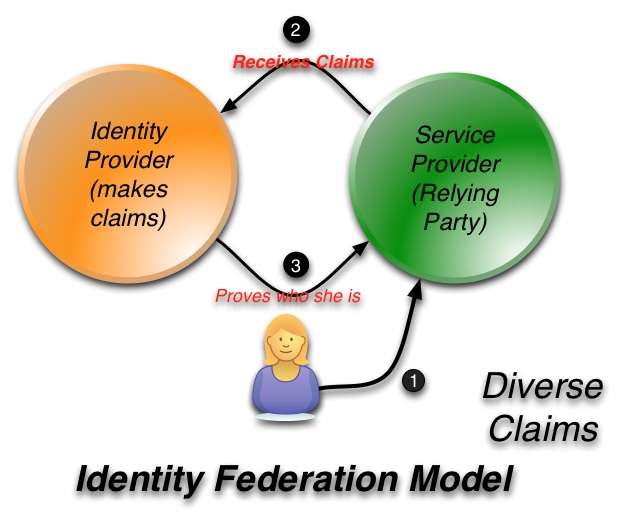
Figure 2: Identity Federation Model
Figure 3 shows the scenario with diverse people with diverse relationships with different IPs. When you add diverse and numerous types of devices — cell phones, tablets, laptops and so on — it even makes the case stronger as to why the current federated identity model is reaching its limits.
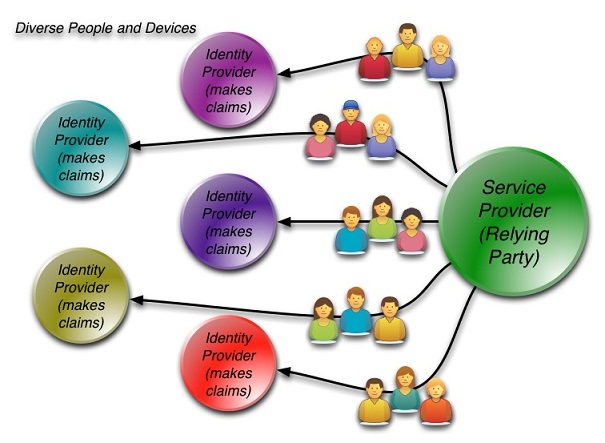
Figure 3: Diverse People and Devices
So if the Federated Identity model doesn’t work, what will? Figure 4 shows one school of thought were a single IP can somehow grow big enough and inclusive enough, it can manage all of the identity claims of all entities. This architecture is both frightening and poorly thought out. People and organizations need to have the freedom of choice of how their identities are managed and not be locked into an identity management silo of a single provider.
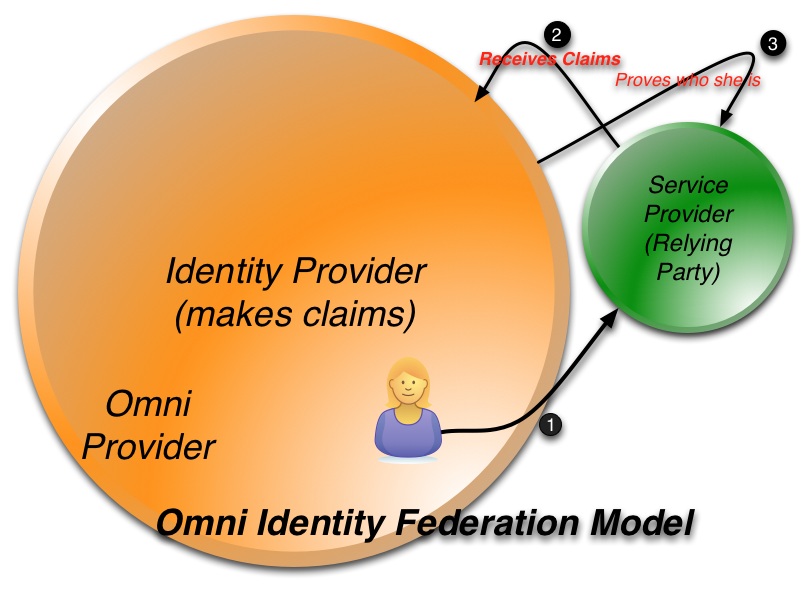
Figure 4: Omni Identity Provider
Figure 5 is another — simpler — graphic showing how a single organization could have federated relationships with multiple constituents. Again, this approach works to a point, but as soon as you consider the impact of the identity explosion brought on by — cloud computing, social computing, mobile computing, and the API economy — this approach simply won’t do the job.
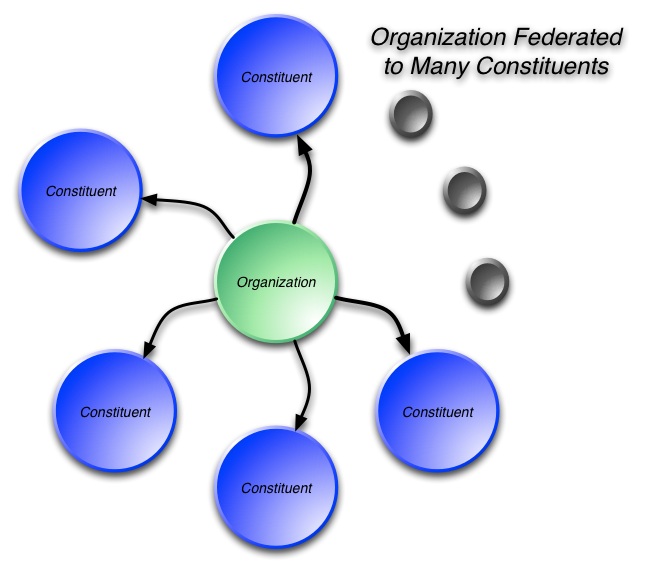
Figure 5: Organization Federated to Many Constituents
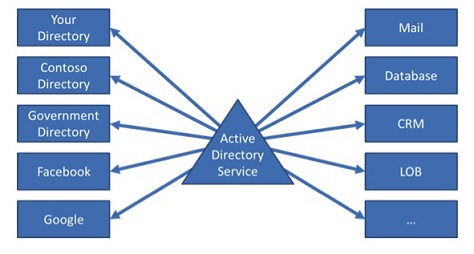
Figure 6 then, shows the simplified notion of the IDMaaS architecture. Any number of organizations, constituents or entities can generate and consume claims through the service in the cloud.
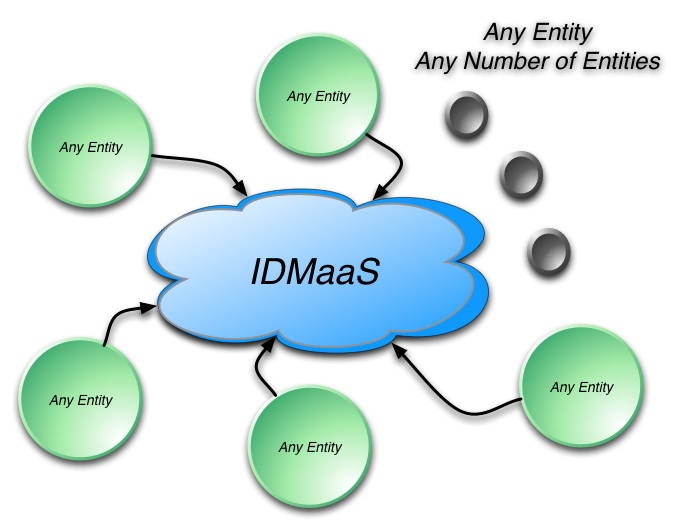
Figure 6: Any Entity and Any Number of Entities
Of course Figure 6 doesn’t very effectively illustrate what the three black dots really mean. With the identity explosion we are talking about, the number of entities that are inevitable are several orders of magnitude bigger than anything we have even thought about up to this point.
We are in new territory, it is very unclear what is going to happen as a result all of this.
The fact that Microsoft seems to be acknowledging this fact and is working with vision to address the matter is highly encouraging.
We are not seeing this kind of vision — or anything close to it — from any other major vendor to date.
Caveats
The biggest problem I see here is Microsoft itself. It isn’t like Microsoft has the reputation of always taking the high road to enhance technology to the benefit of all. To the contrary, Microsoft has the reputation of pretending to take the high road with an “embrace and extend-like” position while executing an exacting and calculating “embrace and execute” practice. Microsoft has become the arrogant elephant to dance with that IBM once was. Microsoft’s past is going to be difficult to shed and it will be a significant effort to convince others that the elephant won’t trample on everyone when it gets the chance.
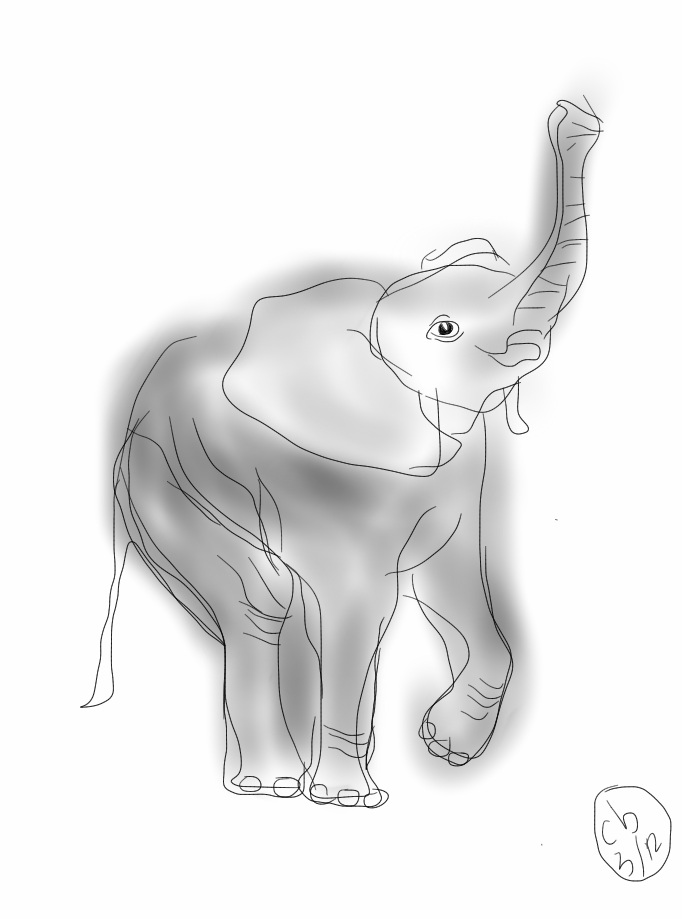
Figure 7: The New Microsoft?
(Source: Craig Burton, drawn on the iPhone with Autodesk SketchBook Pro)
So the tough questions are:
- Can Microsoft really execute on such a brave direction?
- Will Microsoft follow up on allowing true “Freedom of Choice” for the customer? (Think interoperability. i.e. IDMaaS from any vendor, not just MSFT)
- Will the RESTful implementation be usable?
- Can the technology transcend the limitations of Kerberos and LDAP as it moves Active Directory to the cloud?
Summary
My explanation is a simplified one, but if you study it a bit, you will start to see where Microsoft is going.
In short, the vision of an Identity Metasystem based on Identity Management as a Service is brilliant thinking.
The proof will be found in how Microsoft executes.
There is a lot to work out here to show if this can really work. But I believe it can happen. Microsoft is in a good position to garner the expertise to give us this first implementation so organizations and people can start to vet the idea and see if this can really fly.
I will be anxious to watch carefully at the progress of this direction.
I don't mind taking a few knocks from Craig, and don't think this would be the place to respond to them, even if I do think that the interoperable claims based identity technology we have been building and shipping for the last few years is the rocket fuel needed to “transcend the limitations of Kerberos and LDAP as we move Active Directory to the cloud” – one of his main concerns.
But why quibble? Craig really gets what's important. I like the fact that he takes the time to explain why Identity Management as a Service really is a big deal. I suspect part of what he is saying is that it dwarfs the incremental changes we have seen over the last few years because it will impact every mainstream technology.
Craig's points about why infrastructure is hard are all golden, as is his wonderfully simple statement that “the current identity provider-centric world we live in now is broken and simply will not work for the future.”
As for the tough questions, execution can only be judged by looking at what is shipped and how it evolves over time. I'd like to take up the more general, IdMaaS-related questions in upcoming posts. John will be talking in his posts specifically about our RESTful implementation and providing readers with access so they can judge for themselves and give us feedback. At a practical level, we will be making things available incrementally in cloud time, adding breadth and depth as we go on. This whole aspect of cloud innovation makes it hugely exciting.
By the way, I love Craig's elephant – I only wish I could dance so well, metaphorically at least. I also love his graphics: he improved and extended the amateur ones I used in my European Identity and Cloud Conference keynote. So if it's OK with him, I'm going to pitch my own and go with his in my upcoming posts. Thanks Craig.

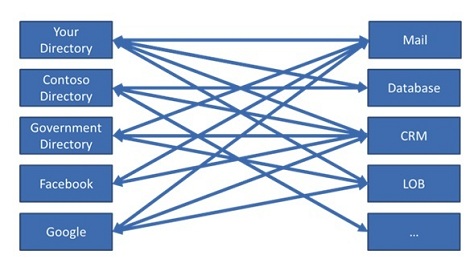









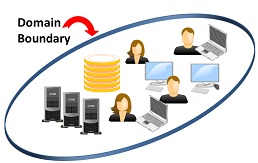 Enterprise identity technology evolved incrementally from mainframe days using the concept of administrative and security “domains”: collections of resources tightly integrated under a single, closed organizational administration.
Enterprise identity technology evolved incrementally from mainframe days using the concept of administrative and security “domains”: collections of resources tightly integrated under a single, closed organizational administration.