Over at Craig Burton, the marketing guru who put Netware on the map and later formed the Burton Group with Jamie Lewis lets loose with a passionate fury that couldn't care less about who has deployed what:
It’s been a week since Microsoft announced that it was never going to release the next version of CardSpace. The laughable part of the announcement is the title “Beyond Windows CardSpace” which would leave you to believe that Microsoft has somehow come up with a better architecture.
In fact Microsoft announced its discontinued development of CardSpace with absolutely no alternative.
Just further evidence of just how irrelevant Microsoft has become.
The news that Microsoft had abandoned CardSpace development is not news to those of us who watch this space, Microsoft hasn’t done Jack with CardSpace for over two years.
It’s just that for some reason Microsoft PR decided to announce the matter. Probably so the U-Prove group could get more press.
Well, that's a bit harsh. Identity selectors like CardSpace only make sense in the context of the other components of the Identity Metasystem – and Microsoft has done a lot over the last two years to deliver those components to customers who are doing successful deployments on a massive scale all over the world. I don't think that's irrelevant, Craig.
Beyond that, I think Craig should look more closely at what the U-Prove agent actually does (I'll help by putting up a video). As I said here, the U-Prove agent doesn't do what CardSpace did. And the problems CardSpace addressed DO remain tremendously important. But while more tightly scoped, for the crucial scenario of sensitive claims that are privacy protected the U-Prove agent does go beyond CardSpace. Further, protecting privacy within the Identity Metasystem will turn out, historically, to be absolutely relevant. So let's not hit on U-Prove.
Instead, let's tune in to Craig's “Little History” of the Identity Metasystem:
In early 2006, Kim Cameron rolled out the Laws of Identity in his blog. Over next few months as he rolled out each law, the impact of this powerful vision culminating in the release of the CardSpace architecture and Microsoft’s licensing policy rocked the identity community.
Two years earlier Microsoft was handed its head when it tried to shove the Passport identity initiative down our throats.
Kim Cameron turned around and proposed and delivered an Identity Metasystem—based on CardSpace—that has no peer. Thus the Identity Metasystem is the industry initiative to create open selector-based digital identity framework. CardSpace is Microsoft’s instantiation of that Metasystem. The Pamela Project, XMLDAP, Higgins Project, the Bandit Project, and openinfocard are all instantiations in various stages of single and multiple vendor versions of the Identity Metasystem.
Let me clear. The Identity Metasystem has no peer.
Anything less than a open identity selector system for claims-based digital identity is simply a step backwards from the Identity Metasystem.
Thus SAML, OpenID, OAuth, Facebook Connect and so on are useful, but are giant steps back in time and design when compared to the Identity Metasystem.
I agree that the Identity Metasystem is as important as Craig describes it, and that to reach its potential it MUST have user agents. I further agree that the identity selector is the key component for making the system user centric. But I also think adoption is, ah, essential… We need to work out a kink or two or three. This is a hard problem and what we've done so far hasn't worked.
Be this as it may, back at Craig's site he marches on in rare form, dissecting Vendor Speak as he goes. Mustering more than a few thrusts and parries (I have elided the juicier ones), he concludes:
This means there is an opening for someone or some group with a bit of vision and leadership to take up the task…
But mark my words, we WILL have a selector-based identity layer for the Internet in the future. All Internet devices will have a selector or a selector proxy for digital identity purposes.
I'm glad to finally see this reference to actual adoption, and now am just waiting for more discussion about how we could actually evolve our proposals to get this to happen.

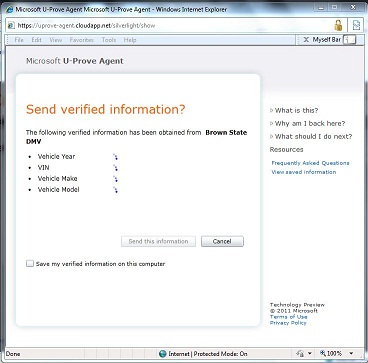 The system takes a number of the good ideas from CardSpace but is also informed by what CardSpace didn’t do well. It doesn’t require the installation of new components on your computer. It works on all the major browsers and phones. It roams between devices. Sites don't have to worry about users “getting a card” before the system will work. And it allows claims providers and relying parties to shape and brand their users’ experiences while still providing a consistent interface for claims approval.
The system takes a number of the good ideas from CardSpace but is also informed by what CardSpace didn’t do well. It doesn’t require the installation of new components on your computer. It works on all the major browsers and phones. It roams between devices. Sites don't have to worry about users “getting a card” before the system will work. And it allows claims providers and relying parties to shape and brand their users’ experiences while still providing a consistent interface for claims approval.


 Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID.
Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID. We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway.
We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway. OK. This is all very nice for Microsoft's apps, but how do other application developers benefit?
OK. This is all very nice for Microsoft's apps, but how do other application developers benefit?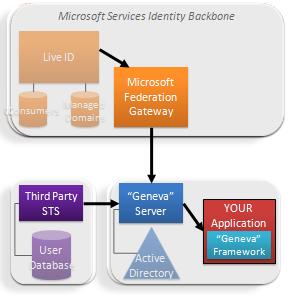 These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm.
These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm. 