Jon Udell put up this thought-inducing piece on the widely discussed Sierra affair earlier this week, picking up on my piece and the related comment by Richard Gray.
Kim Cameron had the same reaction to the Sierra affair as I did: Stronger authentication, while no panacea, would be extremely helpful. Kim writes:
Maybe next time Allan and colleagues will be using Information Cards, not passwords, not shared secrets. This won’t extinguish either flaming or trolling, but it can sure make breaking in to someone’s site unbelievably harder.
Commenting on Kim’s entry, Richard Gray (or, more precisely, a source of keystrokes claiming to be one of many Richard Grays) objects on the grounds that all is hopeless so long as digital and real identities are separable:
For so long identity technical commentators have pushed the idea that a person’s digital identity and their real identity can be tightly bound together then suddenly, when the weakness is finally exposed everyone once again is forced to say ‘This digital identity is nothing more than a string puppet that I control. I didn’t do this thing, some other puppet master did.’
Yep, it’s a problem, and there’s no bulletproof solution, but we can and should make it a lot harder for the impersonating puppet master to seize control of the strings.
Elsewhere, Stephen O’Grady asks whether history (i.e., a person’s observable online track record) or technology (i.e., strong authentication) is the better defense.
My answer to Stephen is: You need both. I’ve never met Stephen in person, so in one sense, to me, he’s just another source of keystrokes claiming to represent a person. But behind those keystrokes there is a mind, and I’ve observed the workings of that mind for some years now, and that track record does, as Stephen says, powerfully authenticate him.
“Call me naive,†Stephen says, “but I’d like to think that my track record here counts for something.â€
Reprising the comment I made on his blog: it counts for a lot, and I rely on mine in just the same way for the same reasons. But: counts for whom? Will the millions who were first introduced to Kathy Sierra and Chris Locke on CNN recently bother explore their track records and reach their own conclusions?
More to the point, what about Alan Herrell’s1 track record? I would be inclined to explore it but I can’t, now, without digging it out of the Google cache.
The best defense is a strong track record and an online identity that’s as securely yours as is feasible.
The identity metasystem that Kim Cameron has been defining, building, and evangelizing is an important step in the right direction. I thought so before I joined Microsoft, and I think so now.
It’s not a panacea. Security is a risk continuum with tradeoffs all along the way. Evaluating the risk and the tradeoffs, in meatspace or in cyberspace, is psychologically hard. Evaluating security technologies, in both realms, is intellectually hard. But in the long run we have no choice, we have to deal with these difficulties.
The other day I lifted this quote from my podcast with Phil Libin:
The basics of asymmetric cryptography are fundamental concepts that any member of society who wants to understand how the world works, or could work, needs to understand.
When Phil said, that my reaction was, “Oh, come on, I’d like to think that could happen but let’s get real. Even I have to stop and think about how that stuff works, and I’ve been aware of it for many years. How can we ever expect those concepts to penetrate the mass consciousness?â€
At 21:10-23:00 in the podcast2, Phil answers in a fascinating way. Ask twenty random people on the street why the government can’t just print as much money as it wants, he said, and you’ll probably get “a reasonable explanation of inflation in some percentage of those cases.†That completely abstract principle, unknown before Adam Smith, has sunk in. Over time, Phil suggests, the principles of asymmetric cryptography, as they relate to digital identity, will sink in too. But not until those principles are embedded in common experiences, and described in common language.
Beyond Stephen O'Grady's piece, the reactions of Jon's readers are of interest too. In fact, I'm going to post Richard's comments so that everyone gets to see them.
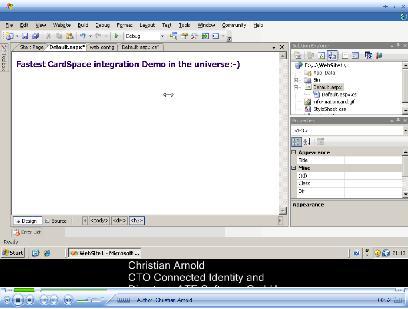 Christian Arnold has now done a video where he shows how simple it is to add Information Card support to the “out of the box” Visual Studio membership provider. He has written some really cool controls.
Christian Arnold has now done a video where he shows how simple it is to add Information Card support to the “out of the box” Visual Studio membership provider. He has written some really cool controls. 
 Your patent commemorative is more than metal and wood – it is tangible evidence that you have made a contribution to this world and future generations. One of our customers, Mr. Hank Cutler, said it best:
Your patent commemorative is more than metal and wood – it is tangible evidence that you have made a contribution to this world and future generations. One of our customers, Mr. Hank Cutler, said it best:
 Once you understand the possibility of breach, you can calculate the associated risks, and build the technology that has the greatest chance of being safe. You can't do this if you don't understand the risks. In this sense, all you can do is manage your risk.
Once you understand the possibility of breach, you can calculate the associated risks, and build the technology that has the greatest chance of being safe. You can't do this if you don't understand the risks. In this sense, all you can do is manage your risk.