Introduction
Since its inception, the Microsoft Passport service has existed in a digital world that is increasingly multi-centered and rich in contexts. This digital world requires the sharing and federation of identities and close attention to matters of user control. These requirements have led Microsoft to evolve the Passport service continuously. To emphasize this evolution, Microsoft is changing the name of the service to something more indicative of its specific contribution to the emerging “identity metasystem”: the Windows Live ID service.
Windows Live and Office Live are Internet-based software services designed to deliver rich, seamless experiences to individuals and small businesses. The offerings combine the power of software with online services to make compelling new tools that complement Microsoft Windows and Microsoft Office products.
Microsoft online services need to know who is interacting with them—just as users need to know that the services themselves are legitimate. This mutual need requires the use of digital identities. The Windows Live ID service is designed to manage identity and trust within the Windows Live ecosystem.
For end users, the Windows Live ID service provides roaming access to the broad array of Microsoft online services. For developers, it enables over 300 million potential online users to access their applications.
What Are Windows Live ID and the “Service”?
A digital ID is a set of claims made by one entity about another.
A Windows Live ID is a set of claims that the Windows Live ID service makes.
These claims can refer to individual users, organizations, devices, and services. Initially, most claims will be based on information stored in accounts the service maintains on behalf of its users, in much the same way that Passport has worked in the past. Moving forward, the service will also rely upon the claims issued by other federated identity providers, transforming them to make sense within the Windows Live ecosystem.
What kinds of claims can a Windows Live ID contain?
- User's e-mail address
- Type of entity (such as organization, group, or namespace)
- Relationships among subjects, such as:
- Parent-child relationship.
- Administrator status or ownership of an organization, group, or namespace.
- Membership in an organization, group, or namespace.
- Authorization for specific scenarios, such as enforcement of parental controls
- User ownership of a public-and-private key pair, for use in peer-to-peer communications
Windows Live IDs that are based on Windows Live ID accounts (as opposed to federated IDs) can be authenticated using traditional user-name/password pairs, strong passwords and security PIN combinations, and smart cards. Windows Live ID will also support the use of self-issued “InfoCards.” For example, users will be able to employ “InfoCards” to access Windows Live Mail. For more information, see “InfoCard” Support later in this document.
The Windows Live ID service also maps federated IDs supplied by other identity providers into a form that works within Microsoft online services. This is done through protocols like WS-Trust, WS-Security, and WS-Federation—widely accepted, royalty-free industry protocols that can be (and have been) implemented on any platform. WS-Security is already an OASIS (Organization for the Advancement of Structured Information Standards) standard, while WS-Trust and other related protocols are in the standardization process now. Because “InfoCards” also implement WS-Trust, the Windows Live ID services federation servers will be able to accept “managed InfoCards” too.
So that customers can access Microsoft online services by using any device, the Windows Live ID service also supports specialized mechanisms (like the Radius protocol) for authentication from cell phones, televisions, and Xbox 360. Through these devices, Windows Live ID also supports applications that range from dial-up service to peer-to-peer instant messaging.
For developers, Windows Live ID provides programmable interfaces that reduce development time on both the client and relying-party server sides, making it easier to develop new identity-aware services for the ecosystem and new client products to access them. The Windows Live ID services are also accessible through soon-to-be-published protocols.
High-Level Architecture
The following figure is a high-level illustration of the ecosystem in the Windows Live ID world.
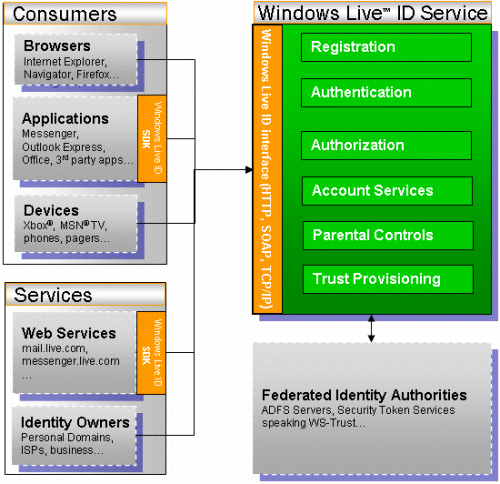
How Does Windows Live ID Relate to Passport?
The Windows Live ID service represents the evolution of Microsoft Passport into a world based on federation. Windows Live ID will be the authentication system for all existing and future Microsoft online services. Relying parties (Microsoft properties and those of close partners) who have implemented Passport will be compatible with the Windows Live ID service.
Another area of evolution is towards support for “rich clients” using Web services. By supporting WS-Trust and “InfoCard,” Windows Live ID will extend its single sign-in framework to the Windows Communication Framework (WCF) employed in many emerging applications.
End users will be offered an automatic upgrade path for using their Passport accounts as Windows Live IDs. Similarly, the Windows Live ID service will be backward compatible with relying parties that have already integrated with the Microsoft Passport Network. However, to take advantage of the new features and scenarios provided by the new Windows Live ID service, relying parties may have to adopt new software development kit (SDK) components and protocols.
How Does Windows Live ID Participate in the Identity Metasystem and Work with “InfoCard”?
Microsoft is working with others in the industry to create an identity metasystem that brings existing and future identity providers into a connected identity ecosystem and empowers end users to control the use of their identities. The Windows Live ID service will participate in the identity metasystem as one identity provider among many, able to accept claims from other identity providers and transform them so they can be used within Microsoft online services. This participation will include acceptance of self-issued and managed “InfoCards.” It will thus provide full support for the “InfoCard” identity model.
Roles of the Windows Live ID Service in the Identity Metasystem
Microsoft has published its vision of a universal identity solution that is inclusive of a plurality of identity operators and technologies—the identity metasystem. In such a metasystem, identity providers, relying parties, and subjects can select, request, transfer, transform, and consume identities through a suite of well-defined and open Web Services (WS-*) protocols. Microsoft is working to implement components of the identity metasystem, as are many other companies in the industry. As a result, various building blocks for the metasystem are being developed. Some of these components will be delivered to end users in the form of software installed and running locally on their computers and devices, while others will be online services.
The design philosophy of the identity metasystem is not to replace the existing identity systems in use today, but instead to bring these existing systems together by enabling interoperation among subjects, relying parties, and identity providers through industry standard protocols. The Windows Live ID service will participate in the identity metasystem as a “managed” identity provider already at Internet scale. Windows Live ID will bring a large base of end users and relying parties to the metasystem, taking us one step closer to Internet-wide identity federation and doing our part to help the industry move beyond the “walled garden” paradigm.
The Windows Live ID service will play several essential roles that are strategic for Microsoft. The service:
- Is an Internet-scale identity provider intended primarily for users of Microsoft online services, which are all relying parties of the Windows Live ID service.
- Is open and issues claims in a form that can be consumed by any relying party, any device, and any other trusted identity authority.
- Serves Microsoft online services as a “claims transformer,” allowing those services to accept identities issued by third-parties. Third-party identity providers include other Internet service providers and managed-identity providers, such as the planned Active Directory Security Token Service (STS).
- Will be the identity provider and federating authority for third party services and software built on top of the Microsoft online services platform.
“InfoCard” Support
“InfoCard” is the code name for the Microsoft implementation of an identity selector for the identity metasystem. “InfoCard” provides a consistent experience for users to manage, control, and exchange their digital identities. It is an important step towards eliminating user names and passwords as the primary mechanism by which users identify themselves. “InfoCard” provides a safer way for users to manage and exchange their digital identity information, helping to protect them from various forms of identity fraud.
For more information, see the InfoCard site in the WinFX Developer Center.
Since Windows Live ID is designed to robustly manage user identities, it will support “InfoCard” when “InfoCard” is broadly available (expected in the fourth quarter of 2006 for Windows XP, Windows Server 2003, and Windows Vista).
The current plan is that Windows Live ID will support both self-issued and third-party managed cards as a mechanism to authenticate users when accessing Windows Live services. Subsequently, Windows Live ID will also issue managed cards to enable users to use their Windows Live ID with third parties.
Together, Windows Live ID and “InfoCard” will enable users to enjoy the rich array of Windows Live services more easily than ever before.
Programmability
The Microsoft online services are designed to become an Internet programming platform for developers to build desktop applications and online services. (For more information about this platform, see the Windows Live Developer Center.)
So Microsoft must make it easy to program for the Windows Live ID service.
To simplify integration on both the server side and the client side, the Windows Live ID service will release software development kits (SDKs) later this year. In addition, the Windows Live ID service uses industry standard protocols. For cloud server-to-server scenarios, the Windows Live ID service exposes programmatic interfaces by way of SOAP services.
The Relying Party Suite (RPS) SDK makes it easier and cheaper to develop a new Microsoft Live service by providing interfaces that prepare authentication requests, decrypt, parse, and validate security tokens, and manage authentication-state cache in a browser session.
But more importantly, RPS reduces operational cost by providing support for configuration refresh—critical for partners that host services from different global geographic locations, and for times when it is necessary to change cryptographic keys.
A second SDK—the Windows Live ID Client SDK—runs on end users’ computers. This SDK makes it easier to write new client applications that understand Windows Live IDs and supports the sharing of authentication state across multiple rich clients and browsers. It also manages short-lived certificates issued by the Windows Live ID Certificate Authority; these certificates can be used in security-sensitive applications such as peer-to-peer communication channels.
Like the Relying Party Suite, the Client SDK supports the automatic configuration and refresh mechanisms critical to accommodating the Windows Live ID services “geo-hosting” plans.
Windows Live Messenger is an example of a client built on top of the Client SDK.
Advantages of the Windows Live ID Service
Through years of developing and operating one of the largest identity providers on the Internet, Microsoft has learned valuable lessons from customers, Internet security professionals, and developer communities worldwide.
Large Scale
The Windows Live ID service is the next-generation version of a system that does over 22 billion authentications per month and is used to access a large set of online services operated by Microsoft and its close partners.
Security
Security is a priority for the Windows Live ID service, which undergoes regular audits performed by independent auditors. Microsoft is committed to investing in security to help protect customers and relying parties against ever-evolving threats.
Quality of Service
The Windows Live ID service is built on top of a highly available infrastructure, including redundant networking elements, front-end and back-end servers, and fault-tolerant software components. The services are continuously monitored by multiple automated agents including internal tools and external monitoring services. Windows Live ID is built on components that have demonstrated a high quality of service.
APIs to Speed and Simplify Deployment
The Windows Live ID service is designed with development support in mind. All functionality is exposed through programmable SOAP interfaces that will be published soon. The Relying Party and Client SDKs ease development efforts for both relying-party services and rich-client applications, and help to deliver robust and efficient components to run on relying party servers or end-user computers. The SOAP interfaces are documented and will be available to all, enabling Windows Live ID services to be used in contexts not using the other SDKs.
Seamless User Experiences
The Windows Live ID service delivers a seamless user experience across client applications and Web browsers accessing relying-party services.



 For those new to Identityblog and looking for an introduction, here is a short interview I did recently with
For those new to Identityblog and looking for an introduction, here is a short interview I did recently with  In recent years, police around the country have started to use powerful infrared cameras to read plates and catch carjackers and ticket scofflaws. But the technology will soon migrate into the private sector, and morph into a tool for tracking individual motorists’ movements, says former policeman Andy Bucholz, who's on the board of Virginia-based
In recent years, police around the country have started to use powerful infrared cameras to read plates and catch carjackers and ticket scofflaws. But the technology will soon migrate into the private sector, and morph into a tool for tracking individual motorists’ movements, says former policeman Andy Bucholz, who's on the board of Virginia-based