Once you have a Certificate Authority, you have a factory for producing certificates. This will let you mint test certificates for your InfoCard relying party (they will also work should you want to experiment with being a managed card provider).
The gotcha is that before they will work on a machine, they have to be hand-installed. Why? They have not been issued by the widely distributed trust root authorities shipped with Window, Macs, and Linux. Thus they don't work “out of the box”. That's why you need for the installation step.
The result is that while perfect for testing and experimentation, these certs won't work as production certs in the real world. There you'll have to go to a commercial provider. But this won't break the bank. My identityblog cert costs quite a bit less $2.00 per month.
We'll deal with this issues in another part of this guide. For now, let's turn to using your factory to create a test cert.
Create a Certificate Request for your machine
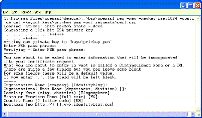
Change directory to the “openssl/democa” directory you made earlier. Run “makereq” to generate a machine SSL key and corresponding certificate request. This time the system will ask for a passphrase to protect the SSL key for which the cert is being requested. In other words, this is a different key, cert and passphrase combination than you used with the Certificate Authority.
When running the script, enter a simple DNS name as the CN (hostname) field. In my case, for example, I used www.identityblog.com as the CN. Don't use the http:// prefix or nothing works!
After running the script, the machine's private key will be written to democa/keys/privkey.pem. Meanwhile a certificate request will be placed in democa/requests/cert.csr.
Create your Certificate
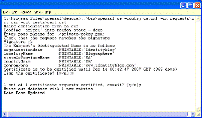
Next, run “makecert” – which puts the certificate request from the last step into the Certificate Authority (i.e. factory) to produce a certificate. You'll be asked for the CA's passphrase:
When this is complete, the cert has been created, and is in “democa/certs/cert.crt”.
If you want to use the cert within IIS
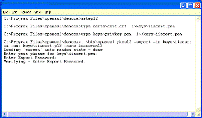
If you want to use the cert in IIS, run “makep12” and get ready for a final conflagration of passprases. This script combines your private key and cert into a single “.p12” file that can be installed as a windows machine cert. To do so it performs a format translation. You will have to supply the machine key's passphrase to decode the “.pem” formatted file so the translation can proceed. Then you will be asked for an export passphrase (the one used to protect it in the new p12 format). I always use the same passphrase – who cares what format the information is in?
“makep12” puts the combined Windows key/certificate file in “democa/keys/iiscert.p12”
Now your openssl machine key is in “democa/keys/privkey.pem”. Your machine cert is in “democa/certs/cert.crt”. Your IIS key/cert combination, if you made one, is in “democa/keys/iiscert.p12”.
Moving the files into the “keys” directory
To use my sample managed card code, create a “keys” directory under your http server's root directory. Move the privkey.pem you just created into “keys/host.key”. Move the cert you just created into “keys/host.crt”. Create a file called “keys/host.pwd” and put the machine key's passphrase into that file. Then the scripts I provide should work with your newly created keys and cert.
Follow instructions elsewhere in this guide if you want to install the combined p12 key into Windows and IIS.
What if you want more certificates?
You've got a certificate factory now, and can make as many certs as you like by going back to the “Create a certificate request” step and running through the process again.