Here's a story by the Canadian Broadcasting Corporation (CBC) on the British Columbia government's IDM project. Dick Hardt of sxip played the key and even charismatic role in developing a catalytic relationship between industry and government.
British Columbia will test a virtual ID “card” that enables citizens to connect with the government's online services more safely and easily, a top technology official said.
The government plans to begin tests on an “information card” early in the new year, said Ian Bailey, director of application architecture for the province's Office of the Chief Information Officer.
The cards are in the early stages, and “there's going to be some challenges,” Bailey said.
An information card is not a card at all: it's more like a document delivered to users’ computers which they can then use to access government websites.
It's meant to replace the current method of access, which involves logging on to a site with a name and password, and has a digital signature that can't be changed or reproduced, Bailey said.
“It will give us better privacy protection for individuals,” he said.
Among other attributes, Bailey said using an information card means:
- The government won't know which sites the user visits.
- The user is in control of shared information.
- The cards won't have to reveal users’ birthdates or addresses, or a student's school. Instead, it could simply confirm the user is over 19, a B.C. resident or a student.
He compared using the card to using a driver's licence for identification since, in both cases, the government does not know what the citizen is doing. Continue reading B.C. to test virtual digital ID card


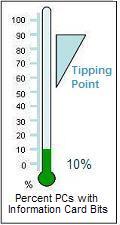 I’ve started publishing a “sockets guageâ€
I’ve started publishing a “sockets guageâ€