The Internet may sometimes randomly “forget”. But in general it doesn't.
Once digital information is released to a few parties, it really is “out there”. Cory Doctorow wrote recently about what he called the half-life of personal information, pointing out that personal information doesn't just “dissipate” after use. It hangs around like radioactive waste. You can't just push a button and get rid of it.
I personally think we are just beginning to understand what it would mean if everything we do is both remembered and automatically related to everything else we do. No evil “Dr. No” is necessary to bring this about, although evil actors might accelerate and take advantage of the outcome. Linkage is just a natural tendency of digital reality, similar to entropy in the physical world. When designing phsyical systems a big part of our job is countering entropy. And in the digital sphere, our designs need to counter linkage.
This has led me to the idea of the “Need-to-Know Internet”.
The Need-to-Know Internet
“Need to Know” thinking comes from the military. The precept is that if people in dangerous situations don't know things they don't need to know, that information can't leak or be used in ways that increase danger. Taken as a starting point, it leads to a safer environment.
As Craig Burton pointed out many years ago, one key defining aspect of the Internet is that everything is equidistant from everything else.
That means we can get easily to the most obscure possible resources, which makes the Internet fantastic. But it also means unknown “enemies” are as “close” to us as our “friends” – just a packet away. If something is just a packet away, you can't see it coming, or prepare for it. This aspect of digital “physics” is one of the main reasons the Internet can be a dangerous place.
That danger can be addressed by adopting a need-to-know approach to the Internet. As little personal information as possible should be released, and to the smallest possible number of parties. Architecturally, our infrastructure should lead naturally to this outcome.
Need-to-Know and Minimal Disclosure
CardSpace is an important step in this direction – offering much less visibility of identity providers onto users’ activities than “redirection protocols” like SAML WS-Federation and OpenID, which reveal the DNS names of all the sites you employ, continuously, in real time. On the contrary, when using self-issued cards, CardSpace transmits no linking artifacts that allow one party to collude with another about your identity.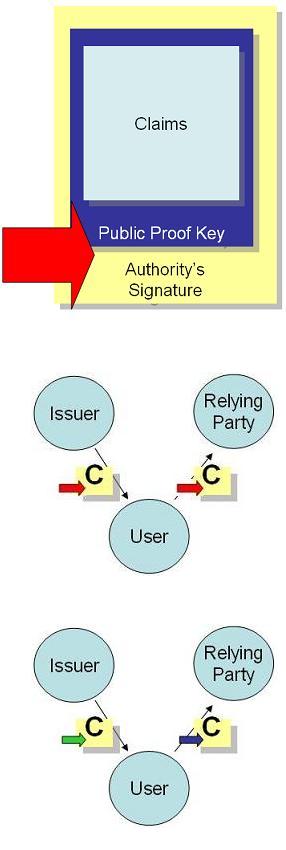
However, with managed cards carrying claims asserted by a third party authority, it has so far been impossible, even for CardSpace, to completely avoid artifacts that allow linkage. (I've treated these issues in depth in my Series on Linkage.) Though relying parties are not able to collude with one another, if they collude with the identity provider, a set of claims can be linked to a given user even if they contain no obvious linking information.
The reason is that to prevent a set of claims from being shared and replayed, we need an identifier and/or “proof key” in it. The authority then needs to sign the identifier and key as well as the claims.
With conventional (e.g. RSA) technology, any set of claims presented to a site will have the signature present, and so can potentially be traced back to a given authentication and token issuance. If a relying party is willing to take its claimset to the identity provider, and the identity provider is willing to investigate, the colluding duo can figure out which user presented which set of claims
Magic Signatures?
But there is good news. Minimal disclosure technology allows the identity provider to sign the token and proof key in such a way that the user can prove the claims come legitimately from the identity provider without revealing the signature applied by the identity provider.
I've tried to represent that in the diagram where the set of claims ‘C’ has a “green signature” applied by the issuer, but what is conveyed to the relying party is a proof (“blue signature”) that doesn't reveal the green signature.
If the relying party takes the “proof” back to the issuer, the issuer won't recognize it, because all it knows about is the “green signature”. So it can't be linked to specific user unless the claims themselves contains overt identifying information. In other words, no linking artifacts.
The RSA of Privacy
Stefan Brands has been working on this minimal disclosure technology since the early 1990’s. As I've said on many occasions, his system is incredibly well thought through and elegant. The explanation I've just given touches on only one aspect of a really impressive technology grounded in innovative cryptography (more information on the Credentica web site).
In my view, Stefan's technology, called “U-Prove”, is the equivalent in the privacy world of RSA in the security space. It does things we wouldn't have otherwise thought possible. At one time “public key” was considered an oxymoron – but the properties of RSA were so compelling they completely changed our thinking about keys.
The same, I think, is true of the zero knowledge proofs and “blinded signatures” Stefan has perfected. When you first hear about their capabilities, you say, “Well, that's impossible”. But if you look into the math, its not. It actually works.
Funny. A few weeks ago, Bruce Schneier wrote a brief blog post saying:
“Cryptographer Stefan Brands has a new company, Credentica, that allows people to disclose personal information while maintaining privacy and minimizing the threat of identity theft.
“I know Stefan; he's good. The cryptography behind this system is almost certainly impeccable. I like systems like this, and I want them to succeed. I just don't see a viable business model.
“I'd like to be proven wrong.”
I think Microsoft's acquisition of Stefan's technology and patents does prove him wrong – and that he'll be happy about this.
Our goal is that Minimal Disclosure Tokens will become base features of identity platforms and products, leading to the safest possible intenet. I don't think the point here is ultimately to make a dollar. It's about building a system of identity that can withstand the ravages that the Internet will unleash. That will be worth billions.
My interest is in building the very best identity system we can build, and making it a simple option for people to deploy, so that the binary opposition of “privacy” and “security” is replaced by a deep understand that “need-to-know” and minimal disclosure produces both the most secure and the most privacy friendly Internet.
Products and Roadmaps
It is really early in the cycle for us to have worked out a roadmap. Getting the right user experience to accompany capabilities like this is not trivial. But our plan is to integrate U-Prove into both the Windows Communication Foundation (WCF) and CardSpace. When that happens, all products built on the WCF Framework will easily support U-Prove. That would include our own servers as well as those by third parties.
As always, adopting U-Prove doesn't mean we reject other identity technologies. No one is going to take away your RSA keys! It means there is a new option available in building the identity metasystem, an option that is ideal for Government and medical applications, child protection, military systems, and identity outsourcing to name just a few. The idea is that we need a spectrum of solutions, reaching all the way from systems for public and social networking identity to those for sensitive information where need-to-know is the key factor.
You can probably tell how excited I am about this. I want to thank the people within Microsoft who made this possible by agreeing to take the plunge that will bring ground-breaking privacy technology to the market.
Best of all, I look forward to the great things the collaboration with Stefan, Christian and Greg can bring, and the fun we will have building the most secure identity system possible while at the same time taking privacy protection to whole new levels.
For more information, check out Stefan's blog. You should also look at PrivacyImperative to see the perspective of my colleagues from the Microsoft Privacy Team. Adam Shostack, who worked closely with Stefan at Zero Knowledge in Montreal, comments here.
