Even if the true meaning of uber-geek is “incomprehensible”, my last comment on the use of delegation in VRM was a real winner in terms of terseness. I was discussing Whit's notion that he wanted to give Amazon access to his behavior at Netflix, Powell's and lastfm – the goal being to improve Amazon's relationship with him by revealing more about himself as a complete person. So I'll try to unfold my thought process.
If you ponder the possible architectures that could be used, it becomes clear, as usual, that the identity aspects are the hardest. Let's build a little picture of the parties involved. Let's say the user (I know, I should be calling Whit a “customer”), shares his behavior with Amazon and Powell's. Now let's call some subset of his behavior at Powell's “BP“. Whit would like an outcome that would be modelled in the following diagram, assuming for the moment that U->A:BP just represents Amazon asking Powell's for the customer's relevant information.
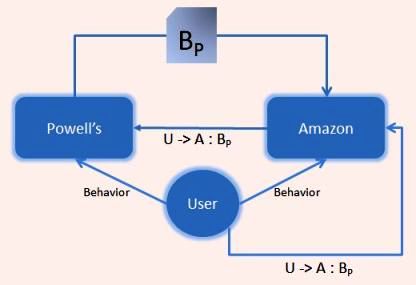
But how does Powell's know that Whit really wants it to release information to amazon.com but not snooper.com? How does it know that the amazon.com which calls for information is really the same Amazon that Whit was dealing with? Why should Powell's ever take the privacy risk of releasing information to the wrong party? What would its liability be if it were to do so? Can it protect itself from this liability?
When I mentioned delegation, I meant that while the user is “behaving” at Amazon, it gives Amazon a “coupon” that says “User delegates to Amazon the right to see his Behavior at Powell's”. I represent this as U->A:BP, where:
- U is the user;
- A is Amazon;
- P is Powell's; and
- B is behavior
Amazon can now present this coupon to Powell's, along with cryptographic proof that it is the “A” in the coupon. By retaining this coupon and auditing any release, Powell's can indemnify itself against any accusation that it released information to the wrong party – and better still, actually defend the user's privacy.
‘Breaking up is hard to do.’
I have left two of the most important questions for another time. First, is it really necessary (or advisable) for Powell's to know that the Whit is sharing information with Amazon, rather than “some legitimate party”? Second, how does Whit revoke the permission he has granted to Amazon if he decides the time has come for them to “break up”?
But without even opening those cans of worms, it should be evident that, for reasons of privacy, auditablity and of liability reduction, everyone's interests are served by making sure no service ever acts as an end user. In this example, Amazon continues to act as Amazon, and even if its access is one day anonomized, would would always be identified as “the user's delegate”. The approach constrasts starkly with current approaches – as spooky as they are cooky – in which users release their credentials on “good faith” and eventually, if enough secrets are shared, anyone can be anyone.
Note: The notation above is my own – please propose a better one if it is just as simple…

Couple of comments on delegation en its use.
1. We _always_ use delegation: if I use a piece of software on my machine to login to a site or application, it is that piece of software (e.g. the CardSpace client) that does the transaction, claiming it is authorized to do so. But if the software is compromised, it may misrepresent me or even somebody else. Is there a fundamental difference between software on my (owned? managed? checked?) machine and a machine under somebody else’s control?
2. The example of Amazon and Powell sharing ‘behavior’. I smell vast containers of worms. For instance, why would Powell share their knowledge with a competitor – even if the customer endorses or stimulates them to do so? Only, it seems, if they get something in return, like the same data held by Amazon. But how are they going to weigh up their respective knowledge assets? And speaking about knowledge, the customer might be shocked to learn what his merchant has chalked up as ‘behavior’. Sites can run little tests to see how sensitive a customer is to price, what pictures his unconscious prefers to click, whether she is a reader (give her pages with lots of text) or a restless clicker, whether he frequents price comparison sites (from referral URLs) and should be offered the best deal possible or can be lured with ‘list’ prices, etc. Unlikely that a site wants to share that information, unlikely too that they even could do so in a language that is understood by another site. And of course, nothing here is under user control – he has no idea what kind of information the merchant has on him.
A more realistic schema would be that I build my own profile. I could use local software that monitors my doings and offers to add it to my profile. Search terms are one source of “things I’m interested in”. The profile could be segmented (like I now have multiple identities) and I control to whom I show what part of my profile. In fact, the profile segments are extensions (additional attributes) to my identities. No need for delegation (beyond what I said in 1. above).
Interesting, I have an simalar idea iof an architecture like this: I call it “Transaction Centric Services”. Would be nice to discuss the architecture. Yóu will find my post here:http://www.codecomplete.de/blogs/digitalidentity/archive/2007/03/12/13.aspx