Here's a site dedicated to phishing control that has produced a bizarre mashup that I find fascinating – Web 2.0 meets Magnum PI. It combines information from the Anti-Phishing Working Group with novel visualization techniques and animation so you can analyse the topologies of phishing trips over time.
A phishing message arrives in your mailbox, pretending to be from a bank, or from an etailer such as eBay or Paypal. It directs you to a web page and asks you to enter your password or social security number to verify your identity, but the web page is not one actually associated with the bank; it's on some other server.
InternetPerils has discovered that those phishing servers cluster, and infest ISPs at the same locations for weeks or months.
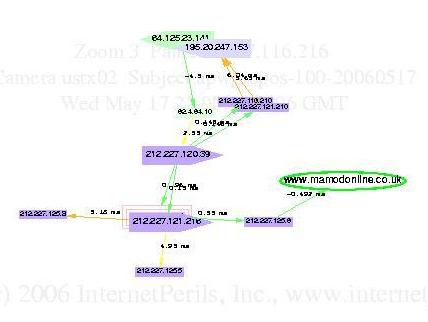
Here's an example of a phishing cluster in Germany, ever-changing yet persistent for four months, according to path data collected and processed by InternetPerils, using phishing server addresses from the Anti-Phishing Working Group (APWG) repository.
Figure 1: A Persistent Phishing Cluster
The ellipses in this animation represent servers; the boxes represent routers; and the arrows show the varying connectivity among them. Colors of boxes reflect ownership of parts of the network. Times are GMT.
The animation demonstrates a persistent phishing cluster detected and analyzed by InternetPerils using server addresses from 20 dumps of the APWG repository, the earliest shown 17 May and the latest 20 September. This phishing cluster continues to persist after the dates depicted, and InternetPerils continues to track it.
Graphs were produced using PerilScopeâ„¢, which is InternetPerils‘ interactive topology examination interface, based upon the GAIN platform.
Go to their site to see the actual animated mashup.

One thought on “Anti-phishing Mashup”
Comments are closed.