The Burton Group's CEO, Jamie Lewis, discusses the OSP and what it means for the identity community:
As has been widely reported, Microsoft announced its Open Specification Promise last week. A lot of folks have already posted about it (see here, here, and here ). But, given the overall importance of the announcement to the identity community, I wanted to make our thoughts on the subject known, and to give credit where it’s due. (Note: This entry is cross posted at both my blog and our new Identity and Privacy Strategies blog.)
In summary, Microsoft has decided to offer the Open Specification Promise (OSP) for the Web services protocols that support CardSpace in particular, and the InfoCards architecture in general. The OSP provides an alternative to Microsoft’s “reasonable and non discriminatory/royalty free†(RAND/RF) licensing agreement, which most open source developers didn’t like. As I understand it, the OSP essentially provides an assurance that Microsoft won’t sue anyone implementing the specifications covered by the document. So developers don’t even have to agree to a license; they can implement the covered specifications without fear of being sued. (With certain, mostly comprehensible exceptions.)Before I comment on the OSP, however, let me first provide the disclaimer almost every technologist I talk with about licensing issues gives me: I’m not a lawyer, and so my comments should in no way be construed as having legal weight. (If you’d like to see an analysis of the OSP document from a legal perspective, see Andy Updegrove’s excellent post from last week.) But Microsoft’s announcement has more than legal ramifications. Microsoft’s move could have a significant impact on the market, and that’s where we come in.
In short, the OSP is a significant, positive step forward for both Microsoft and the community working to create a better identity infrastructure for the Internet. The people who have been tirelessly advocating the move within Microsoft deserve an enormous amount of credit for making it happen. (Kim Cameron deserves some special recognition at this point in what has been a long process.) At this, point, one of the most significant obstacles to widespread development around the InfoCard architecture has been removed, and that’s good news for everyone involved.
Some Background
I’ve been following the InfoCard effort for a long time with a great deal of interest, primarily because I’ve always thought it was a great idea. But I also had some concerns about how it would be received in the market, at least early on. Circa 2002, it was fair to say that, given Microsoft’s history, any idea the company put forward for addressing the identity problem—regardless of its merit—would likely meet large amounts of skepticism and, at least in some cases, outright resistance from many market players.
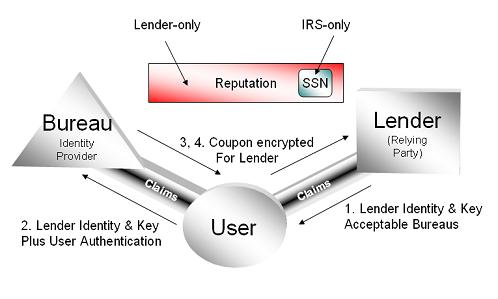
From the first time he ever spoke with me about the functionality we now know as CardSpace, for example, Kim has been consistently insistent about the need for and importance of cross-platform support. I certainly agree that a consistent user experience—regardless of the operating system and device a person chooses to use—is profoundly important to addressing the identity problem. But I’ll have to admit that I wondered many times if Microsoft would really let Kim do what he thought needed to be done. And as I talked with other folks about InfoCard as the concept began to take shape, I heard more than a few people express varying degrees of skepticism about Microsoft’s true intentions or Kim’s ability to convince the powers that be to move in a more open direction.
But by decidedly atypical and relentless means, Microsoft has done a great deal of what seemed nearly impossible only a few years ago, overcoming the skepticism and building good will. Consequently, there is a palpable and sincere desire on the part of a lot of people to implement the InfoCard technologies. And three or four years ago, many of these people wouldn’t have even considered working with Microsoft on a beer run, much less an identity system.
Still, licensing was a huge obstacle to seeing that good will and intention translated into demonstrable action and working code. With only a few exceptions, everyone I talked to over the last six months or so—from open source developers to commercial software companies—indicated that until the licensing issue had been put to bed, they really couldn’t (or wouldn’t) build anything. And they had a point. Were I in their shoes, I would insist on clear licensing terms as well.
Enter the OSP
With the OSP, then, Microsoft has taken what is for it a bold step, removing one of the most significant obstacles to widespread InfoCard development. The OSP makes it clear that Microsoft isn’t laying some elaborate and sinister trap for everyone, that it truly is offering something of significant value to the industry and a huge opportunity to developers looking to build better identity management systems.
Yes, there are still some details to work out (I’ll get to those in a moment). And yes, neither CardSpace nor InfoCard’s supporting system are slam dunks in today’s transitional market place. But the OSP is concrete evidence that even those with valid reasons to doubt Microsoft’s sincerity are running out of excuses for ignoring InfoCard. Without it, the overall InfoCard effort was stymied. With it, the InfoCard effort can move forward in the way Kim has always intended. And for that both Kim and Microsoft deserve recognition and gratitude.
About Those Remaining Issues Several folks have commented that it’s not just the specifications that matter, but the implementation details. And they’re right. (While I’ve heard similar things from a few people, most of these issues are summarized in the Higgins project’s draft response to the OSP.)
Microsoft has published an implementation guide for CardSpace, but the details it includes on how to implement the specifications covered by the OSP aren’t covered by the OSP. (You can find the guide, as well as other details on implementation, on MSDN.) In particular, there are schema and meta-data models that are crucial to getting what Paul Trevithick calls “functional equivalence†with CardSpace on other platforms. The CardSpace user interface is an equally important issue. While efforts like the Higgins Trust Framework may not copy the CardSpace UI down to every pixel, interoperable implementations must emulate the basic sequence of events in the CardSpace interface (what Kim Cameron has called “ceremonyâ€) if we’re to get the common user experience to which Kim aspires. These implementation details must be covered by the same kind of promise.
But if Microsoft can accomplish what’s embodied in the OSP as it now stands, then it seems reasonable to assume that what remains is haggling over details, that the licensing issue is finally on a downhill path. In other words, the fat lady has sung, and we’re just waiting for the coda. And now the onus has shifted to those who have professed a willingness to implement InfoCard technologies and interoperate with Microsoft if the licensing details could be favorably resolved. Microsoft is living up to its end of the bargain, and now it’s your turn. Those who’ve already started development, without waiting on the licensing issues, have some advantage. My advice to those who have been waiting? Get busy.