My blog was hacked over the weekend. It was apparently a cross-site scripting attack carried out through a vulnerability in WordPress. WordPress has released a fix (Version 2.3.1) and I've now installed it.
ZDNet broke the news on Monday – I was awakened by PR people. The headline read, “Microsoft privacy guru's site hacked”. Fifteen minutes of fame:
IdentityBlog.com, a Web site run by Microsoft’s chief architect of identity and access, has been hacked and defaced.
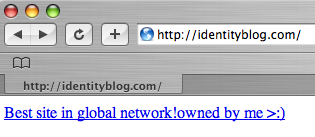
The site, which is used by Microsoft’s Kim Cameron to promote discussion around privacy, access and security issues, now contains an “owned by me†message and a link to a third-party site (see screenshot).
Naturally there were more than a few congratulatory messages like this one from “Living in Tension” (whose tagline says he has “Christ in one hand, and the world in the other):
Several years of working in the Information Technology world have unintentionally transformed me into a OSS , Linux, security zealot…
… Tasty little tidbits like this are just too good to be true
I wonder if he would have put it this way had he known my blog is run by commercial hosters (TextDrive) using Unix BSD, MySQL, PHP and WordPress – all OSS products. There is no Microsoft software involved at the server end – just open source.
The discussion list at ZDNet is amusing and sobering at the same time. Of course it starts with a nice “ROTFLMAO” from someone called “Beyond the vista, a Leopard is stalking”:
This one was priceless . How can Microsoft's Security Guru site get hacked ? Oh my all the MS fanboys claim that Microsoft products are so secure .
<NOT!>
But then “ye”, who checks his facts before opening his mouth, has a big ‘aha’:
How can this be? It runs on UNIX!
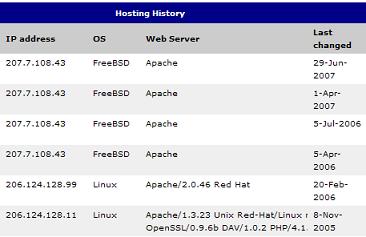
FreeBSD Apache 29-Jun-2007
Why it's the very same BSD UNIX upon which OS X is based. The very one we've heard makes OS X so ultra secure and hack proof.
This is too much for poor “Stalking Leopard” to bear:
How about explaining as to what a Microsoft employee would be doing using a UNIX server ? I don't think microsoft would be too happy hearing about their employee using… more than their inherently safe IIS server.
Gosh, is the “Stalking Leopard” caught in a reverse-borg timewarp?
By this point “fredfarkwater” seems to have had enough:
What kind of F-in idiots write in this blog? Apple this or MS that or Linux there….. What difference doesn't it make what OS/platform you choose if it does the job you want it to? A computer is just a computer, a tool, you idiot brainless toads! A system is only as secure as you make it as stated here. You *ucking moron's need a life and to grow up and use these blogs for positive purposes rather than your childish jibbish!
But as passionate as Fred's advice might be, it doesn't seem to be able to save “Linux Geek”, who at this point proclaims:
This is a shining example why you should host on Linux + Apache .
For those who still don't get it, this shows the superiority of Linux and OSS against M$ products.
Back comes a salvo of “It's on Unix”, by mharr; “lol” by toadlife; and “Shut up Fool!” by John E. Wahd.
“Ye” and marksashton are similarly incredulous:
You do realize that you just made an idiot of yourself, right?
Man you are just too much. I'm sure all of the people who use Linux are embarassed by you and people like you who spew such nonsense.
Insults fly fast and furious until “Linux User” tells “Linux Geek”:
I really hope you know just how idiotic you look with this post! What an ID10T.
It seems the last death rattle of the performance has sounded, but then there's a short “second breath” when “myOSX” has a brainwave:
Maybe he moved the site after it got hacked ???
After that's nixed by “ye”, “Scrat” concludes:
So it appears that dentityblog.com was being hosted by TextDrive, Inc using Apache on FreeBSD.
Bad Microsoft!
The truth of the matter is very simple. I like WordPress, even if it has had some security problems, and I don't want to give it up.
My site practices Data Rejection, so there is no “honeypot” to protect. My main interest is in having an application I like to use and being part of the blogosphere conversation. If I'm breached from time to time, it will raise a few eyebrows, as it has done this week, but hopefully even that can help propagate my main message: always design systems on the basis they will be breached – and still be safe.
Although in the past I have often hosted operational systems myself, in this project I have wanted to understand all the ins and outs and constraints of using a hosted service. I'm pretty happy with TextDrive and think they're very professional.

I accept that I'm a target. Given the current state of blogging software I expect I'll be breached again (this is the second time my site has been hacked through a WordPress vulnerability).
But, I'm happy to work with WordPress and others to solve the problems, because there are no silver bullets when it comes to security, as I hope Linux Geek learns, especially in environments where there is a lot of innovation.