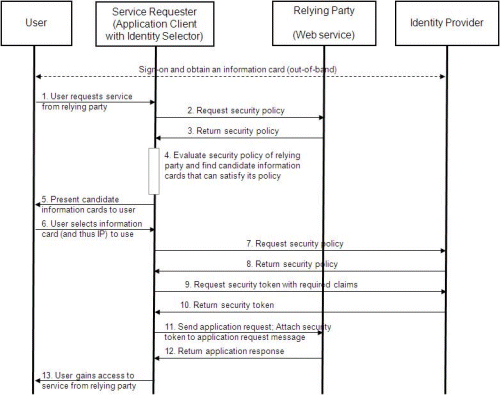
It's great to see mainstream publications really taking the time to understand and convey the issues of digital identity and privacy. A recent article in the Economist discussed the Laws of Identity at length. Cambridge researcher Ross Anderson and others are quoted as well. Here's an excerpt that gives you a sense for the full article:
Internet users have become used to providing personal information to any convincing-looking box that appears on a screen. They have little idea of either the technology that helps to provide electronic security in practice or the theoretical principles that determine whether it will work. According to Mr Cameron, “there is no consistent and comprehensible framework allowing them to evaluate the authenticity of the sites they visit, and they don't have a reliable way of knowing when they are disclosing private information to illegitimate parties. At the same time they lack a framework for controlling or even remembering the many different aspects of their digital existence”…
Cybercrime discredits the use of the internet not only by business but by government too. Mr Cameron suggests rethinking the whole issue, starting from the principle that users may be identified only with their explicit consent. That sounds commonsensical, but many big government databases do things differently. Britain's planned central records for the NHS, for example, will assume consent as it combines all the medical records held in local practice databases.
The second principle, says Mr Cameron, should be to keep down the risk of a breach by using as little information as possible to achieve the task in hand. This approach, which he calls “information minimalism”, rules out keeping information “just in case”. For example, if a government agency needs to check if someone falls into a certain age group, it is far better to acquire and store this information temporarily as a “yes” or “no” than to record the actual date of birth permanently, which would be much more personal and therefore more damaging if leaked.
Third, identity systems must be able to check who is asking for the information, not just hand it over. How easy it is for the outside world to access such information should depend on whose identity it is. Public bodies, Mr Cameron suggests, should make themselves accessible to all comers. Private individuals, by contrast, should be protected so that they have to identify themselves only temporarily and by choice…