From the Internet Governance Forum, via Ralf Bendrath's blog:
The workshop on privacy and identity we held together with the LSE information systems group this morning sparked an interesting discussion.
Christian Möller gave some examples of how privacy is not only important in itself, but how it also is a necessary condition for freedom of expression.
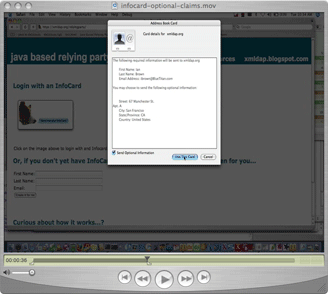
Microsoft’ Jerry Fishenden presented their InfoCards concept and the “7 Laws of Identity” as one approach on how to handle user data based on different credentials. While most of the panelists agreed that this is a good basis for a start, and especially welcomed the company's recent efforts to make it more privay-friendly, Jan Schallaböck and Mary Rundle pointed at one major drawback: Once you have sent your personal information to a company – no matter if through InfoCards or another system – you can not control what happens with it afterwards.
Jan, who is with the data protection authority of the German land of Schleswig-Holstein, therefore presented the ideas, concepts and systems developed in the EU-funded Privacy and Identity Management in Europe (PRIME) project as an alternative.
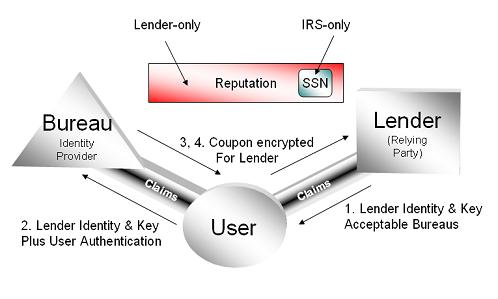
Their model is that user data given to web service providers will have “sticky privacy policy†attached to it in the form of meta-data. This meta-data will move with the personal data and can help ensure that it is only used or tranferred in a way the user has agreed to.
Mary from NetDialogue suggested (having) a similar way as the Creative Commons license: Privacy Policies should be human readable, lawyer readable, and machine readable. The advantages would be that the users can better decide how they “licence” the use of their data to other parties. Mary even presented a very nice series of icons that symbolize different use policies. This approach might be one way to address the failure or “myth of user empowerment”, as Ives Poullet called it.
Stephanie Perrin, research director at the Office of the Privacy Commissioner of Canada, finished by saying that the privacy community has to become much more involved in international technical standardization processes. As always, time was too short. Therefore, we will discuss a collaborative follow-up process later this evening.
Actually, the “sticky privacy policy” notion can be implemented by identity providers using version 1 of Cardspace – it doesn't limit the token types that can be exchanged. A new type of token that includes metadata about use policy is a good example of why this flexibility is useful. I support the idea.
Maybe Jan Schallaböck and Mary Rundle are aware of this, but are talking about the self-issued identity provider used to “bootstrap” Cardspace. In v1.0, it does not have this kind of metadata built in to it.
I look forward to collaborating with Mary and Jan to create the kinds of visual and metadata systems now being discussed. I don't actually see PRIME as being “alternative” in any way to the work I've been doing – we have the same goals.