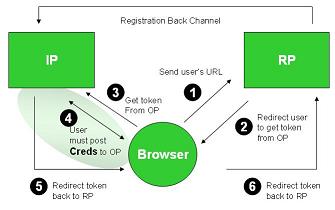
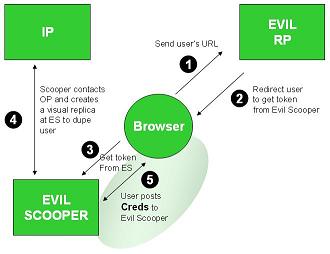
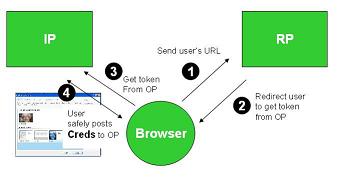
Here are some smart comments by =Andy.Dale of ooTao on how Information Card identity selectors like CardSpace and Higgins should work with XDI and i-names. Andy has played an important role in introducing OpenID to ISPs and his comments bear directly on the convergence theme we've been discussing:
I wrote this missive in an email thread about using CardSpace with i-names I thought I should share it with you too:
IMHO the use cases that i-names support are a super set of the use cases that cardSpace supports… All of the digital identity usecases where someone else's wants to refer to me they need to use a globally unique identifier to identify me. Now I could keep giving people (services) my email but I'd much rather give my i-name. When a party has my i-name they can bootstrap ANY functionality that I provide. This is very different from cardSpace.
CardSpace is REALLY good at doing authentication (on Vista clients). Here's where I'm going to go out on that limb… I-names aren't bound to any specific authentication mechanism, they can be used in SAML they can be used in OpenID, but they can be used in any number of other schemes as well. A managed i-card with a signed assertion from the i-broker that this i-name has been validated as belonging to this card holder seems to me to be just as valid a mechanism to authenticate an i-name as any.
Use case:
I go to Evite (the i-name enabled Evite) and say I want to invite =joe to my party. NOTE: CardSpace has no mechanism for me to identify ‘Joe’; I HAVE to know a global identifier for him. Now Evite can look up =Joe's invitation SEP (could be his contact service, an email or other). Later =Joe wants to look at his invitation at Evite so he goes to the site and logs in with the convenence of the cardSpace paradigm. I don't think that using cardSpace authentication diminishes the value of the i-name in doing what it is good at doing.
So once cardSpace/higgins is broadly available we are going to need to define an attribute type so that an RP can ask for an i-name (or should it ask for an xri?). We are also going to have to provide the list of parties that should be trusted to assert i-name ownership (self asserted ‘this is my i-name’ should NOT be trusted); presumably XDI.org could publish that list.
So in summary… I think that people NEED i-names; they are just too useful in too many usecases. I DONT think that authentication mechanism is a good place to focus on the value of i-names, I would go as far as to say that this is one of the biggest mistakes that we in the i-name community have made. Once you have authenticated that the principle is the valid user of i-name that's where the value starts, not stops. So authenticate by whatever means the RP wants, and then look at all the cool services that can happen.
By the way, I've been using my =Kim.Cameron i-name for a couple of years now – ever since I started this blog. It has been a life-saver. It has been my email conduit to my readers and allowed me to interact personally with many people all over the world – without ONE piece of spam.
So I would be a fool not to be a big supporter. And more broadly, I'm a fan of =Drummond.Reed‘s thinking about identifiers. He and his associates have thought more deeply about what identifiers need to be than anyone else in the world.