Introducing Windows CardSpace This article introduces the set of new Windows capabilities called Windows CardSpace (formerly “InfoCard”), which provides a standards-based solution for working with and managing diverse digital identities. A Deeper Look at Windows CardSpace In this Security Briefs, Keith Brown drills into Windows CardSpace (formerly “InfoCard”) and demonstrates how to create a relying party and a client. Video: Windows CardSpace Explained Ever wonder what Windows CardSpace (formerly “InfoCard”) is all about? Nigel Watling (Technical Evangelist) and Andy Harjanto (Program Manager) explain it in this Channel 9 video with a lot of time spent on the whiteboard. Getting started with Windows CardSpace Step by step instruction on how to build federated identity applications using Windows Communication Foundation and Windows CardSpace (formerly “InfoCard”). In addition, this new Federated Identity & Access Resource Kit for Sept 2005 CTP includes samples to build Security Token Services (STS). (Link currently broken – Kim) Introduction to Information Cards and Internet Explorer 7.0 (in C#) This sample contains 4 exercises demonstrating how to use CardSpace to get a digital identity from a user via Internet Explorer, updated for RC1 and beyond. Included in this sample is the code to the TokenHelper class, which allows relying party websites to decrypt security tokens. The Laws of Identity Defining a set of fundamental principles to which any universally adopted, sustainable identity architecture must conform, the “Laws of Identity” were proposed, debated, and refined through an open and continuing dialogue on the Internet. Microsoft's Vision for an Identity Metasystem The Identity Metasystem is an interoperable architecture for digital identity that assumes people will have several digital identities based on multiple underlying technologies, implementations, and providers. Channel 9 Interviews Kim Cameron The folks from Channel 9 talk to Kim Cameron about identity. The Identity Blog Check out Kim Cameron's Identity Weblog where he discusses the Laws of Identity and other topics around Web services and identification. A Guide to Integrating with Windows CardSpace v1.0 Learn how digital identities can be integrated into a user-centric identity framework, based on the concept of an Identity Metasystem, which promotes interoperability between identity providers and relying parties with the user in control. A Technical Reference for Windows CardSpace v1.0 in Windows A technical reference for the schema employed by and the mechanisms implemented in the Windows client Windows CardSpace (formerly “InfoCard”) system. A Guide to Supporting Windows CardSpace v1.0 within Web Applications and Browsers Learn about the web interfaces utilized by browsers and web applications that support the Identity Metasystem. The information in this document is not specific to any one browser or platform.
Category: Blog
Listening & Engaging with Intent
More delices from Deborah Schultz:
My latest mantra:
Everyone step away from the keyboard and Engage with Intent in “offline community”
My friend Marc Canter
 Marc Canter at Broadband Mechanics/People Aggregator really threw me for a loop today.
Marc Canter at Broadband Mechanics/People Aggregator really threw me for a loop today.
What can I say? He has a fantastic blog, that seems to be getting more and more concise. And unlike most people who blog about their work, he has a “Marc Canter's friends” pane. I'm pretty sure these are personal friends, not professional ones. But just as a joke, I wrote, “I was hurt not to be listed as one of your friends. I guess I need to arrange some more seafood chowder?”
But be careful what you say to Marc Canter. I don't know what happened – my words sent Marc into a long remeniscence. I don't think I know anyone so full of positive energy – and he wears it close to the surface too – where it belongs.
I'm sure everyone knows that the things people give me credit for accomplishing are the product of lots of people pushing in the same direction, both inside Microsoft and out. Marc is one of them, and I really value his friendship Here's what he wrote:.
Somewhere along the way – I wrote up a list of friends – and I did not (apparently) include Kim Cameron’s name on the list.
First of all – I’m sure Kim understands – as I’ve made a lot of friends along the way – in my travels and dealings. But most of these relationships are personal and not business oriented as well. That fateful 1-2 punch is something both powerful and frightening. Cause if you can influence someone to do the right thing AND he wants to do it anyway – well then you got a force of nature that can’t be stopped.
Over 2.5 years ago Kim came to us (me, Dick Hardt, Phil Windley, Doc and a few others) and told us of his dream. A world where Microsoft would GIVE the world key technology to enable disparate Identity systems to inter-connect together. A world where a theoretical backplane for Identity systems – would enable any all to come along and play in the same park.
Needless to say this has been incredibly influential in my thinking since then. I owe a debt of thanks to Kim for instilling in me the belief that this sort of idealistic world can exist in our future.
OpenID is perfect for this sort of world, as is the Liberty Alliance and Shiboleth. It now looks like Yahoo’s BB Auth is also perfect for this sort of distributed federated world of tomorrow. And needless to say Microsoft’s Infocards system is also perfect for this – and is baked into every copy of Vista.
Kim blogs at the Identity Blog and came up with the 7 Laws of Identity – which are a litmus for quality and honesty in the world of Identity.
The guy has an air of grace, humility and honesty to him. After hearing him give his pitch I decided to give him the benefit of the doubt and support his efforts. If indeed Microsoft could achieve all the things Kim claims they were gonna do, then indeed that would prove that Microsoft was changing and that we should support them in their attempts at inter-connecting all identity systems together.
So last month Kim goes and gets MIcrosoft to release 35 pieces of IP – “into the public domain†(well OK – it wasn’t the public domain – but they are “promising to never charge for it†– which is better than Google’s GData.)
He actually got it done. He did what he said he was gonna do!
So from where I’m sitting – my entire future and all of our futures – owes some debt of thanks to Kim. He’s the fucking man!
So I just wanna shout out to my FRIEND Kim Cameron. “Wassup homeboy?â€
“Let’s go have some fine Istrian cucine when you’re here for Web 2.0.â€
He really gets what I'm trying to do.
More on iTunes and Modern Times
Cory Doctorow wrote to say:
Kim, it appears that the four tracks you couldn't burn were video- files that probably couldn't be burned to a redbook CD, though the UI is still inexcusably confusing.
But there's still something rotten in Denmark.
If you go to buy the plastic CD at Amazon, here is the track list you see. Check it out. There are two disks – an Audio CD (Disc 1) and a DVD (Disc 2):
Track Listings
Disc: 1
- Thunder On The Mountain
- Spirit On The Water
- Rollin’ and Tumblin’
- When The Deal Goes Down
- Someday Baby
- Workingman's Blues #2
- Beyond The Horizon
- Nettie Moore
- The Levee's Gonna Break
- Ain't Talkin’
- Blood In My Eyes
- Love Sick
- Things Have Changed
- Cold Irons Bound
Dsc: 2
- Cold Irons Bound (Unreleased live version from Masked & Anonymous)
- Blood In My Eyes
- Things Have Changed
- Love Sick (From The Grammy Awards)
In other words, Amazon says the audio CD includes the audio tracks corresponding to the videos you get on the second disk. Isn't that what you would expect?
The virtual product doesn't let you do the same thing. Who cares if it's not DRM on the audio – but instead, DRM on the video? I'm unable to strip the audio off the video to burn it to a CD.
I think iTunes (or is it Sony?) should have structured their download the way they did with the molecular set – giving you all the audio tracks, and letting you copy them to a CD.
As Cory says, the iTunes user interface is – in this one case – incredibly confusing. But in truth, even if iTunes fixed it, I wouldn't be happy with the Dylan album experience. When I download an album I want the equivalent of the molecular product – with all of its 14 tracks, or whatever it's supposed to have.
Meanwhile, Alex J wrote to me from England.
Alex apparently doesn't think that videos have an audio track, or that I should expect to be able to put the soundtrack on an audio CD the way Sony did in the brick and mortar world (the miracles of modern science!). He writes:
mmmm.. I don't see any DRM problems at all. I don't see any errors on the part of iTunes anywhere. I don't see …. well, shall I tell you what I DO see?
I see a loud mouthed idiot getting hysterical over the fact that he (she?) is trying to burn 4 bonus video – VIDEO – tracks to an audio CD and is being told by iTunes that it can't be done.
Funny that.
Now, stop frothing at the mouth, go and burn tracks 1 through 10 (ie. the audio tracks, you know, the music?), and r-e-l-a-x. Oh, and don't forget to put up a retraction of your silly rant 🙂
I guess “frothing” is not inaccurate, though hauling out the word “bonus” to legitimize the iTunization of the last four songs is a bit much – as is the implication that they don't contain “music”.
Getting down to brass tacks, the trouble is that Blood In My Eyes and Things Have Changed are pretty decent songs (you know, those audio things), and I don't want them caged up inside the proprietary iTunes environment.
WordPress vulnerability at identityblog
Sun's Rohan Pinto has spent a fair amount of time this week using a recipe that has been discussed in the Blogosphere recently to hack into my blog, which runs WordPress 2.0.1, and then apologizing for it (I appreciate that, Rohan).
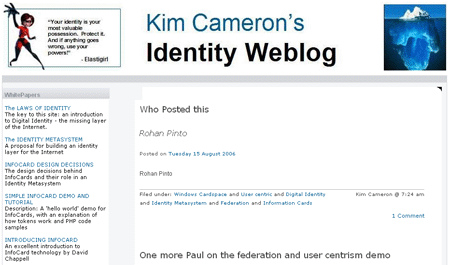 He was able to use a vulnerability in WordPress to employ his “subscriber” account (which normally only grants comment rights) in order to import a fake post onto my site (I've since removed it but it is shown at the right).
He was able to use a vulnerability in WordPress to employ his “subscriber” account (which normally only grants comment rights) in order to import a fake post onto my site (I've since removed it but it is shown at the right).
The exploit used was described about three weeks ago (July 27th, 2006) when Dr. Dave published his “Critical Announcement affecting ALL WordPress Users.” All in all, it was a fairly stern warning. I would have upgraded to a newer version of WordPress but couldn't because I was travelling:
If you are running WordPress as your blogging platform and if you have been trusting enough to leave User registration enabled for guests, DISABLE IT IMMEDIATELY (in wp-admin >> options: make sure “Anyone can register†is not checked).
Additionally, delete or disable ANY guest account already created by people you are not sure about.
Leaving it open and letting people sign-up for guest accounts on your WordPress blog could lead to incredibly nasty stuff happening if anybody so desired. And trust me I am not exaggerating this. So don’t wait a second to disable this option and please relay the message. WordPress dev team has been notified a while back and I dare hope they will soon start acting on it, if only by relaying a similar announcement through the official channel (as well as, of course, releasing a proper patch).
Sorry for the shrill hysterical tone, but this is a big deal. However, disable that one option and you are fine, no need to panic further
[cheers go to Geoff Eby for discovering and bringing this insane security exploit to my attention]
Initially Rohan entitled the post that described the exploit, “Is Cardspace Secure Enough?”. That bothered me, since the exploit had nothing to do with InfoCard or Cardspace or my PHP demo code. Rohan was good enough to later make that perfectly clear:
Pursuant to my prior post. Please do take note of this. I would like to make it crystal clear to everybody that me logging into Kim’s blog and publishing as “him†was NOT a infocard exploit, but rather a “wordpress†exploit…
Please, please, please do note, that this IS NOT a infocard hack.
Conor Cahill read about the exploit and commented:
Access Control is always going to be a responsibility of the entity managing the resource (in this case, Kim's blog is managed by a wordpress installation that he setup on his server, so his server must manage the access control).
The selection of the tool to manage the rescource will be based upon the reliability of the manager and the value of the resource.
I'm sure Kim wouldn't have put his bank account up on wordpress without a lot more testing and perhaps requiring someone else to stand behind it should there be such a problem…
All of this is true, of course, with the exception that my blog usually has more in it than my bank account. Further, in the case of WordPress, it is the application that manages the security, not the underlying operating system or environment (in this case a LAMP stack) or hardware.
Of course, I didn't choose WordPress because it was the most secure solution in the world; I chose it because it was an interesting blogging tool, with a lot of cool features, and would help me learn about the issues confronting people on non-Microsoft platforms so I could have a more inclusive view of identity problems. And it has been great for those purposes.
You might think I would be abandoning WordPress. But I won't. I like it and want to continue to explore what it is like to work with it, and help make it better. To me the real lesson in all of this is that the approach to remote operations used in WordPress – and almost all web-based applications – is just not adequate. The more you know about all the exploits that are possible in the http world, the more you want to run headlong into the world of Web Services, where each transaction has its own security environment, in the sense that the security environment travels with each message and operation. In the same way, SOA moves the control of authorization from the application to the operation definition process, so creative application authors like those who built wordpress, don't have to take sole responsibility for all the subtle security problems that will inevitably arise as we move further into the virtual world.
I take it for granted that given all my pontification about identity and security my site will be used in creative ways. So I have no ill feeling toward Rohan. The important thing is the conversation and the learning that come out of this.
So to rephrase Conor, in this case, the selection of the tool to manage the rescource will be based upon an analysis of the risks and benefits of using an emerging technology to reach others working on the issues.


