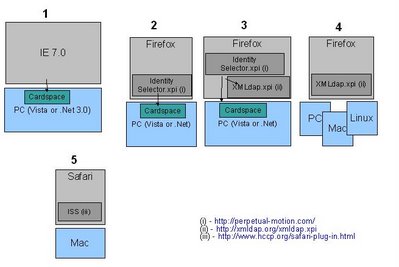
Despite the puns in his first paragraph, this piece by James Kobielus is very interesting, and sums up a lot of the conversations he has been having with people involved in the identity milieu:
“First off, I'd like to suggest that what we should be focusing on is not ‘user-centric identity’, per se, but ‘internet-scalable identity metasystems’ (a thought that Andre ping'd me on and Dick got me to take to hardt). What are the principles for making our identity metasystems truly internet-scalable? Could it be that user-centricity (however defined) is a necessary (but perhaps not sufficient) condition for internet-scalability?
“Now, let's look back to that previous post where I enumerated the main internet-scalability questions that Mr. Hardt laid out for our consideration:
- How do we scale up user-centric identity schemes, in which claims/attributes flow through and are forwarded by the user, so that they work on an open internet scale, not just within self-contained federations or circles of trust?
- How do we enable the free movement of claims from anywhere to anywhere?
- How do we extend lightweight identity management to the “long tail” of websites that don't and won't implement a heavyweight trust/federation model such as SAML or Liberty requires just to do chained/proxied authentication?
- How do we leverage the same core universal lightweight internet design patterns–i.e., REST using URIs and HTTP/HTTPS–to do internet-scale ubiquitous identity?
“Now I'm going to slightly shift the context for a moment to Kim Cameron's “laws of identity,” and then attempt to map that, plus Hardt's concerns, back to the notion of what it takes to make an identity metasystem truly internet-scalable. First, what I'll do is just republish Kim's actual written principles, but in a different order:
- Consistent Experience Across Contexts: The unifying identity metasystem must guarantee its users a simple, consistent experience while enabling separation of contexts through multiple operators and technologies.
- Pluralism of Operators and Technologies: A universal identity system must channel and enable the inter-working of multiple identity technologies run by multiple identity providers.
- Human Integration: The universal identity metasystem must define the human user to be a component of the distributed system integrated through unambiguous human-machine communication mechanisms offering protection against identity attacks.
- User Control and Consent: Technical identity systems must only reveal information identifying a user with the user’s consent.
- Minimal Disclosure for a Constrained Use: The solution which discloses the least amount of identifying information and best limits its use is the most stable long term solution.
- Justifiable Parties: Digital identity systems must be designed so the disclosure of identifying information is limited to parties having a necessary and justifiable place in a given identity relationship.
- Directed Identity: A universal identity system must support both “omni-directional†identifiers for use by public entities and “unidirectional†identifiers for use by private entities, thus facilitating discovery while preventing unnecessary release of correlation handles.
“Now, I'll reclassify/regroup/rewrite these principles into three higher-order principles:
- Abstraction: An internet-scalable identity metasystem must provide all end- and intermediary entities (i.e., users, identity agents, IdPs, RP/SPs, identity brokers, etc.) with a consistent, abstract, standardized , lightweight, reliable, speedy, and secure experience/interface across all use cases, interactions, credentials, protocols, platforms, etc while enabling separation of identity contexts across myriad domains, operators, and technologies.
- Heterogeneity: An internet-scalable identity metasystem must enable seamless, standards-based interoperability across diverse identity use cases, interactions, design patterns, credentials, protocols, IdPs, RP/SPs, platforms, etc.
- Mutuality: An internet-scalable identity metasystem must ensure that all end- and intermediary-entities (i.e., human users, identity agents, IdPs, RP/SPs, identity brokers, etc.) can engage in mutually acceptable interactions, with mutual risk balancing, and ensure that their various policies are continually enforced in all interactions, including, from the human user’s point of view, such key personal policies/peeves as the need for unambiguous human-machine communication mechanisms, privacy protection, user control and consent, minimal disclosure for a constrained use, limitation of disclosures to necessary and justifiable parties, and so on and so forth.
“Now, how would conformance to these three wordy uber-principles contribute to internet-scalability? Well, abstraction is the face of the universal interoperability backplane of any ubiquitous infrastructure (be it REST, SOA, ESB, or what have you). And heterogeneity is the fabric of any hyper-decentralized, federated, multidomain interoperability environment. And mutuality (i.e., a balancing of rights, responsibilities, risks, restrictions, rewards, etc.) is essential for any endpoint (e..g, the end user, an RP/SP, etc.) to participate in this heterogeneous, abstract environment with any degree of confidence that they can fend for themselves and actually benefit from plugging in.
“User-centric identity got going as an industry concern when it became clear that federated identity environments are not always mutual, from the end user's point of view. In other words, under “traditional” federation, some “attribute authority” (not necessarily under your or my direct control) may be coughing up major pieces (attributes) of our identity to unseen RP/SPs (also not under our control) without consulting us on the matter. In other words, those RP/SPs can selectively deny us access to the resources (i.e., apps, data, etc.) we seek, but we often can't selectively deny them access to the resources (i.e., our identity attributes) that they seek. Doesn't seem like a balanced equation, does it?
“Now, tying all this back to Dick's key design criteria for the identity metasystem (in summary): open, free, lightweight, ubiquitous interaction patterns. Seems to scream for abstraction plus heterogeneity plus mutuality, which are necessary and, taken together, sufficient conditions for internet scalability.
“In other words, necessary for the identity metasystem to be universally feasible, flexible, interoperable, implementable, extensible, and acceptable.
I think James makes good points.
Certainly one of the main things that will get us to the identity big bang is correcting the way earlier systems “disappeared” the user. You can see this in the enterprise domain-based systems, where the domain was all-powerful, and it was just assumed that a user was an artifact of one single administrative domain. We now realize we need more flexible constructs.
And you can see it in consumer systems as well.
Why did we all do this? It depends on the context. In the consumer space, I think, for example, it was assumed that customers would be loyal to the convenience of a “circle of trust” set up by portal operators and their suppliers. There was nothing innately wrong about this, but it is just one scenario seen from one point of view.
From the individual customer's point of view, the “circles of trust” should really have been called “circles of profit” between which they were supposed to choose. As Doc Searls says, this isn't the only customer relationship which is possible! Basically, we're talking very last-century stuff that didn't understand the restructuring impact of the web – and these ideas now have to grow into a much wider context. This is a world of really deep relationships with customers, not of forced confinement.
So a big “correction” was in the cards, and the popularity of the “user-centric” view derives partly from this. But there are other forces at play, too. People can talk about “user agents operating on our behalf” as much as they want. But who decides what “our behalf” really is? We need as individuals to control those agents – delegate to them as James says – and keep them from getting “too big for their britches…”
So my basic thesis is not that there shouldn't be agents and services operating on our behalf – or that I would support an architecture that made this impossible. It is that all these services and agents must begin and end by being under the user's control, and we need a consistent technology to achieve that.
I totally buy the notion that a web site gets to decide who accesses it, and what the rules of engagement are for that to happen (“trust is local”). So the user's control with respect to her interests do not diminish a service's control with respect to its interests. Should we call this mutuality? I think what we really have is a mutual veto – both the user and the site being visited can set whatever bar they want before they back out of the transaction. To me, in a world of competition, this remains control.