Caleb Baker, Ruchi Bhargava and a group of their colleagues on the CardSpace team have set up a new blog by techies for techies, called CardSpace: Behind the Code. It warms my heart to see the team members reaching out to make direct contact with other developers and engineers who are adopting the technology or creating versions on other platforms. So often developers in big companies are caught behind a wall of gauze.
They begin with a post that talks in depth about a change in CardSpace that I first announced in June here. Basically, without in any way decreasing the security of high end sites, we have made it markedly easier for bloggers and others whose sites don't represent a financial honeypot to accept information cards:
“CardSpace in .Net Framework 3.0 required that sites deploying CardSpace always have a SSL certificate. This meant that every site that wanted to use CardSpace was forced to deploy an https site.
“Based on customer feedback, we have decided to relax this requirement for the next release of CardSpace (currently available in .NET Framework 3.5 Beta 2). We realize that there are some sites like blogs which would like to use CardSpace, but consider the SSL requirement to be a deployment blocker.
“Now, if you have a website that you want to add CardSpace support to, all you need to do is add the object tag to the page and you are done.
“In addition to requiring .Net Framework 3.5 beta 2 or later [on the windows client – Kim], a new version of icardie.dll is required to use this new feature. This will ship with Vista SP1 and an upcoming update to IE7.
“CardSpace does behave differently for http vs. https sites. When CardSpace is invoked from an http site, CardSpace will inform the user about the lack of an SSL connection and the security implication of this. (Also, note the new streamlined look of this window.)
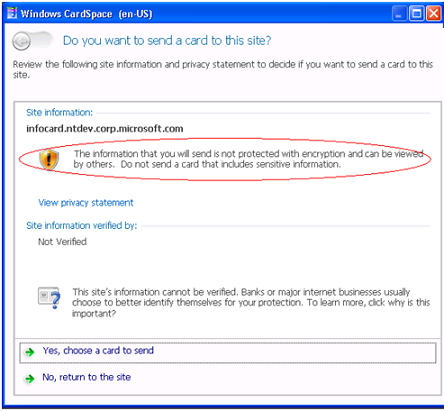
“In addition, managed card issuers can decide if the card they issued can be used on sites that do not support SSL. This can be done by adding the following element to the .crd file.
If this element is specified then the card can only be used on a site that has a SSL certificate. The card will not ‘light up’ when the user is on an http site.
“A point to be noted is that cards that were issued for last release of CardSpace will light up on http sites as they will lack this new element. In that case, the IP STS can make a decision on whether to release a token based on the identity of the recipient sent in the RST message…”
[Continues with changes in algorithms here.]
“Great to hear that you are listening to our feedback :). Thanks!”
Meanwhile, the MSDN blog site they're on doesn't yet seem to show any signs of supporting Information Cards for leaving comments. Maybe I'm just missing it, or maybe Caleb can drum up some info on when that is going to be turned on.

 In a bizarre case of Information Card Fever sweeping through Germany, he
In a bizarre case of Information Card Fever sweeping through Germany, he