Mathew Martin, who writes Mostly Mr. SQL, clearly detests PKI certificates more than almost any living person. He finds CardSpace guilty by association in a piece called GRRRR! CardSpace. What a useless steeming pile…
Ok. Cardspace/Infocard is like OpenId. Password-less access to websites (or password-fewer access).
BUT
1. You must use SSL. Even if you just want to secure your application against your clueless neighbor. That is a minimum of $40.
2. You must decrypt the response on an account with NTFS access to the private key. The NT Network Service account is not likely to have read access to the private key on a hosted account. Good luck explain how and getting co-operation from your hosting provider.
3. Decryption must be done under FULL TRUST. Many hosted accounts only let you run in medium trust and don’t let you create COM+ dlls, put stuff in the GAC, etc.
[Items 2 and 3 might not even be a good idea. If the world at large manages to use your web application to maliciously download your SSL cert, I suppose they could do something evil, like pretend they are you]
4. To get rid of the “the website isn’t secure for banking or ecommerce†you have to spend $1000 on an EV SLL cert. Oh, sure, pocket change.
5. And who is issuing managed cards? I can get an SSL based cert from Thawte that says I am the person that controls my email account, but I can’t find anyone who issues managed infocards anywhere.
I’ve about realize that I–a computer profession and programmer, will not be able to implement InfoCard/Cardspace in any form, not for my blog, not for my hobby website, nothing. Either one has $1040 and ones own entire server or nothing.
If only the top 10 biggest websites can overcome the hurdles posed by infocard, what we are going to see is 5 websites accept infocard and everyone else (mom & pop websites) continue to use passwords and user ID’s. InfoCard will have a minimal impact on how authentication is done.
This is going to drive small websites into using OpenId. Consumer will rapidly gain a few dozen OpenId cards. The rising ubiquity of OpenId–which doesn’t try to be a waterproof authentication method–will take over the world, relegating InfoCard to “that way you logon to Live.com servicesâ€.
Come on Microsoft, when are we going to be able to run CardSpace/Info card in “real world†mode?
[Thanks to Self-issued.info for the logo] [Actually, I take that back, it is a Microsoft trademark. The purple box is has a substantial amount of IP self legislation that goes with it. According to MS’s lawyers, I am currently in violation of usage guide lines for the icon. Let’s see how Microsoft silences critics of InfoCard.]
Let's start with the CardSpace requirement that a relying party support SSL. I agree with Mathew that requiring use of SSL and PKI is overkill for the type of blogging and hobbyist use cases he describes. While my identityblog certificate is fairly inexpensive (thanks to godaddy.com), the extra cost associated with it at textdrive (which hosts my system) is around $100.00 per year because of the need to have a dedicated outward facing IP address. I don't mind the cost too much, since I know there are people who will hit on my site and I like the extra protection. But this really isn't appropriate for everyone.
This underlines the fact that identity and the identity metasystem involve a continuum of use cases and technologies – and we have to embrace the whole continuum. By making certificates mandatory, we cut the continuum in half. Luckily, we can fix that before we get into the wide deployment phase.
My conclusion is that rather than hard-wiring the requirements for identification of a relying party into the identity selector, we should have allowed each identity provider to decide what minimal requirements were appropriate.
This ends up having advantages both at the low value and high value ends of the spectrum.
For example, a bank's IP might decide to only release information to a relying party with an Extended Validation (EV) certificate. If so, CardSpace would not illuminate the associated information card if an EV certificate were not in use at the relying party site. [EV certificates are only granted to companies or other organizations after they follow an extensive procedure for proving their legitimacy.]
Meanwhile, a blogging reputation identity provider might be happy to release reputation to any site the user proposes, certificate or no certificate.
Of course, the relying party is always free to use a certificate and gain the extra protection that provides.
This change is actually part of CardSpace 1.1 – which people should be able to start experimenting with very soon now. When combined with the release of great toolkits for all the important languages, I think this will bring quite a bit of lift-off.
As for point 4), let's look at what the CardSpace advisory actually says:
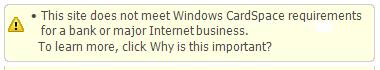
I think there's a big difference between “a major internet business” and a site doing “ecommerce”. When I buy a tee-shirt from Mathew I don't expect him to be EV. If he were trying to sell thousand dollar cameras, I would feel differently. I'd want him to either be well identified, or to work through a site like eBay that would provide another way of establishing his reputation. And in this case, I want to make sure I'm really talking to eBay, so once again would like to see an EV cert.
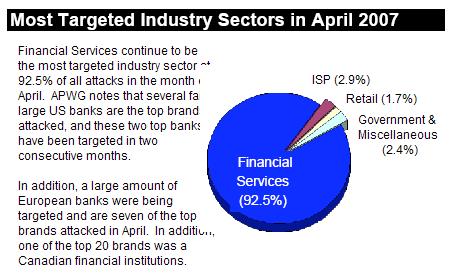
I don't think any “major internet business” or bank will have any difficulty whatsoever covering the cost of an EV cert. The idea of using the superior certs came directly from them, since they're the ones whose users get phished. I don't understand why, given his earlier rant against the poor validation proceedures in conventional certificates, Mathew rails against our support for EV. Part of his earlier criticism of EV certs is that the browser doesn't show the meaning of the cert properly, a problem CardSpace has solved. Consider this recent Anti-Phishing Working Group report:
As for who is issuing managed cards, you'll be seeing many outfits doing it as we move toward the InfoCard tipping point. We're in the sockets and ecosystem phase of Information Cards, but I can tell you many players get the potential of the technology and are integrating it into product.
As for OpenID versus Information Cards, I don't see them as opposites. Go to signon.com today and you'll see it supports use of Information Cards for OpenID authentication. This is nice because it gets you InfoCard safety along with OpenID long-tail support. Going forward, I think you'll see most OpenID vendors supporting OpenID managed cards that work with OpenID sites.
As for the Information Card Icon, our intention is that it be available to everyone who supports the technology. There has been pushback on the language around the icon, and we'll be figuring out how we can get this thing right. In the meantime, I wouldn't be worried about using it on a teeshirt or to criticise us – but I would be worried about using it at a phishing site.

 In a bizarre case of Information Card Fever sweeping through Germany, he
In a bizarre case of Information Card Fever sweeping through Germany, he