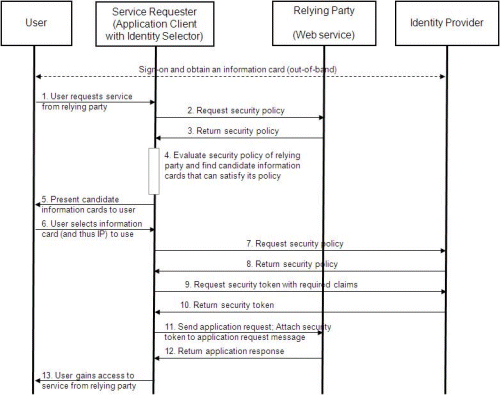
This list of claims is taken from the Identity Selector Interoperability Profile, and specifies a set of claim (attribute) types and the corresponding URIs defined for some commonly used personal information…
The base XML namespace URI that is used by the claim types defined here is as follows: http://schemas.xmlsoap.org/ws/2005/05/identity/claims
For convenience, an XML Schema for the claim types defined here can be found here.
8.5.1. First Name
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Type: xs:string
Definition: (givenName in RFC 2256) Preferred name or first name of a subject. According to RFC 2256: “This attribute is used to hold the part of a person's name which is not their surname nor middle name.”
8.5.2. Last Name
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
Type: xs:string
Definition: (sn in RFC 2256) Surname or family name of a subject. According to RFC 2256: “This is the X.500 surname attribute which contains the family name of a person.”
8.5.3. Email Address
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Type: xs:string
Definition: (mail in inetOrgPerson) Preferred address for the “To:” field of email to be sent to the subject, usually of the form @. According to inetOrgPerson using RFC 1274: “This attribute type specifies an electronic mailbox attribute following the syntax specified in RFC 822.”
8.5.4. Street Address
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/streetaddress
Type: xs:string
Definition: (street in RFC 2256) Street address component of a subject?s address information. According to RFC 2256: “This attribute contains the physical address of the object to which the entry corresponds, such as an address for package delivery.” Its content is arbitrary, but typically given as a PO Box number or apartment/house number followed by a street name, e.g. 303 Mulberry St.
8.5.5. Locality Name or City
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/locality
Type: xs:string
Definition: (l in RFC 2256) Locality component of a subject?s address information. According to RFC 2256: “This attribute contains the name of a locality, such as a city, county or other geographic region.” e.g. Redmond.
8.5.6. State or Province
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/stateorprovince
Type: xs:string
Definition: (st in RFC 2256) Abbreviation for state or province name of a subject?s address information. According to RFC 2256: “This attribute contains the full name of a state or province. The values should be coordinated on a national level and if well-known shortcuts exist – like the two-letter state abbreviations in the US – these abbreviations are preferred over longer full names.” e.g. WA.
8.5.7. Postal Code
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/postalcode
Type: xs:string
Definition: (postalCode in X.500) Postal code or zip code component of a subject?s address information. According to X.500(2001): “The postal code attribute type specifies the postal code of the named object. If this attribute value is present, it will be part of the object's postal address – zip code in USA, postal code for other countries.”
8.5.8. Country
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/country
Type: xs:string
Definition: (c in RFC 2256) Country of a subject. According to RFC 2256: “This attribute contains a two-letter ISO 3166 country code.”
8.5.9. Primary or Home Telephone Number
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/homephone
Type: xs:string
Definition: (homePhone in inetOrgPerson) Primary or home telephone number of a subject. According to inetOrgPerson using RFC 1274: “This attribute type specifies a home telephone number associated with a person.” Attribute values should follow the agreed format for international telephone numbers, e.g. +44 71 123 4567.
8.5.10. Secondary or Work Telephone Number
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/otherphone
Type: xs:string
Definition: (telephoneNumber in X.500 Person) Secondary or work telephone number of a subject. According to X.500(2001): “This attribute type specifies an office/campus telephone number associated with a person.” Attribute values should follow the agreed format for international telephone numbers, e.g. +44 71 123 4567.
8.5.11. Mobile Telephone Number
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/mobilephone
Type: xs:string
Definition: (mobile in inetOrgPerson) Mobile telephone number of a subject. According to inetOrgPerson using RFC 1274: “This attribute type specifies a mobile telephone number associated with a person.” Attribute values should follow the agreed format for international telephone numbers, e.g. +44 71 123 4567.
8.5.12. Date of Birth
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/dateofbirth
Type: xs:date
Definition: The date of birth of a subject in a form allowed by the xs:date data type.
8.5.13. Gender
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/gender Type: xs:token
Definition: Gender of a subject that can have any of these exact string values –
- 0 (meaning unspecified),
- 1 (meaning Male) or
- 2 (meaning Female). Using these values allows them to be language neutral.
8.5.14. Private Personal Identifier
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/privatepersonalidentifier
Type: xs:base64binary
Definition: A private personal identifier (PPID) that identifies the subject to a relying party. The word “private” is used in the sense that the subject identifier is specific to a given relying party and hence private to that relying party. A subject?s PPID at one relying party cannot be correlated with the subject?s PPID at another relying party…
8.5.15. Web Page
URI: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/webpage
Type: xs:string
Definition: The Web page of a subject expressed as a URL.