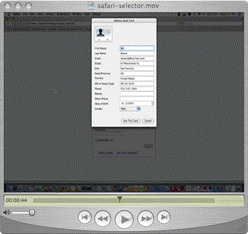
 One of the best moments of the DIDW show, for me, came when Ian Brown, an old friend of Chuck Mortimore, showed us his Identity Selector for Safari.
One of the best moments of the DIDW show, for me, came when Ian Brown, an old friend of Chuck Mortimore, showed us his Identity Selector for Safari.
If you don't know Chuck, he single-handedly wrote a Java-based InfoCard Identity Selector that runs inside Firefox on almost any platform. He gave me a copy, helped me install it on my computer, and it all just works.
Later I'll do a screen capture of Chuck's work since i can run it on my own machine.
But I don't currently have a Mac – so Ian succumbed to my goading and put together a little video so you could see what he's working on.
That's such good news. As he says, “For the faint of heart, or for those running those other operating systems, here's a short screencast of the Safari identity selector in action, authN'ing against Kim Cameron's RP…”
Meanwhile, here's what he says about the actual plugin:
This is currently still at the proof of concept stage, and is lacking most of the features found in the official CardSpace selector from Microsoft. At present, only a single self-asserted card can be selected. The “selector” will currently pull the logged in account's personal information from the AddressBook application, and allow you to use that AddressBook entry as a self-asserted InfoCard with various RPs. It should work with existing installs of Safari, and with most relying parties.
The plug-in itself is a wrapper around Chuck Mortimore‘s Java implementation of an InfoCard token generator. For those of you out there using Firefox, check out Chuck's cross-platform Firefox InfoCard selector.
So download the Safari Plug-In below and give it a spin. Send me any feedback at igb at hccp.org
I'll post new releases here as features are added and bugs are fixed.
Downloads
Currently there are two versions, one for the new Intel-based Apple's, and one for the PowerPC-based machiines. At some point I'll figure out how to get XCode to generate a Universal Binary. (I suppose the PowerPC build might work on the Intel Macs, that's what Rosetta is all about right? But it hasn't been tested on the Intel arch, so YMMV.)
Intel version
http://www.hccp.org/InfocardPlugin.bundle.zip
PowerPC version
http://www.hccp.org/InfocardPluginPPC.bundle.zipInstallation
Installation is pretty simple. After downloading the ZIP file, extract the archive. You should now have a file called InfocardPlugin.bundle. Just copy that to the Library/Internet Plug-Ins directory under your home directory. restart Safari, and off you go.
Despite Ian's self-depricating style I think what he and Chuck are doing is amazing. And it shows what can and will be done. Meanwhile, Apple People, download Ian's plugin and leave comments on my blog.



 Earlier this summer, just before the Burton Group Catalyst conference,
Earlier this summer, just before the Burton Group Catalyst conference,