It's currently hard to locate and install the right software to try out InfoCard on the identityblog but a bunch of intrepid explorers have now actually done it, making me feel a deep wave of geek comraderie.
In fact, the subscription list has doubled since yesterday (doubling once every twenty-four hours may not be sustainable!) And we've had our first identity attack! Things are poppin’ – so to speak – techies bumping into a new technology and a lot of fun.
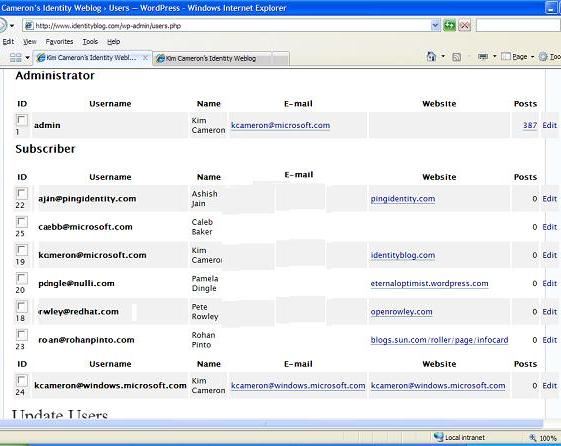
You can see a sanitized list of subscribers here – the uncategorized entry at the bottom is the attacker (more later).
So let me start with Ashish Jain. Looks like he is starting an identity blog called iTickr.com. He calls this posting Welcome InfoCard:
As a core Java / ex-BEA guy (if I only got a penny every time I told customers to stay away from .NET), I never thought I would say this: it's been fun playing with Infocards for the past couple of days. Sure, it takes a lifetime to figure out what you need and what's the right place to download (MS overusage of ‘setup.exe’ doesn't really help)… but once you have that figured out, it's all ‘click’ and ‘play’. Managed to log into Kim Cameron's Identity Blog using my self-issued Infocard. This is what I did:
- Harass my IT guy to get a vanilla m/c with WinXP2 (I wasn't going to risk my own).
- Downloaded (here) and installed WinFX Runtime Component.
- Updated some COM+ Hotfix (the installation process guides you there).
- In my control panel, verified that I have the extra icon ‘Digital Identities’.
- Clicked ‘Digital Identities’ icon and created some dummy infocards (the interface is pretty intuitive).
- Downloaded IE7 from here.
- Accessed identityBlog.com and clicked on login.
- Selected Infocard as the option to login.
- Installed the ActiveX control (it's a test machine so I was little more liberal in clicking ‘Yes’ to every download).
Screen started greying out… (very theatrical… they should add some sound effects too). Picked one of my self-issued inforcard and I'm in.
Some of the screen shots here.
Plan to put together a SP application and hopefully use some managed Infocards in the coming days. Stay tuned.
So cool. Before we go further, let me say that Ashish is totally on the money here in making sure he rounded up a test PC. Please follow his example.
I've actually installed this stuff on my production laptop, which is insane, but this is only because I am prepared to sacrifice deeply to get a feeling for what it's really like to live in an infocard world. (Someone just called me the “Madame Curie of Identity”). I need to understand the experience issues as well as I can.
Be prepared for minor changes with breaking periods before InfoCard goes to release. In case of doubt follow the implementor's guide when it comes to futures.
If you think installing the software is hard, upgrading it is just not supported. So use a dedicated or virtual machine.
I like Ashish's comment that the InfoCard desktop is, well, “…theatrical… they should add some sound effects too”. The goal is to draw the user into a ceremony where he or she will be on the lookout for abnormal behavior – in accordance with the sixth law. And yet, not to do something that would grate on your nerves as you get used to it. It's pretty clean.
OK. Now let's move on to the next new visitor. I'm talking about Caleb Baker. I haven't said enough about my team, and I want everyone to know how much I like and appreciate these foks. They have worked relentlessly to get this stuff out.
Caleb is one of the guys who is most critical to our InfoCard team. He works in the test organization, building automation for the Identity Selector and other components. If anyone knows what components work with what others, it's Caleb!
Testing this kind of project is unbelievably complex given the security issues. Imagine doing UI testing on a product when your test programs can't even see the InfoCard screen (because they are running on a private desktop)! It boggles the mind! But Caleb always seems to be in a positive mood.
One of the great things about Caleb – and his buddies – is how deeply committed he is to the privacy and security aspects of InfoCard. Few architects are fortunate enough to work with people who go so far to make sure theory and high level design principles are being applied in every nook and cranny of a project – with no shortcuts. I'm very grateful.
Finally, last but not least, there is the inimitable Rohan Pinto.
Rohan is from Sun, and blogs about infocards here. He is working on this stuff as a personal initiative at this point, and he's right out there in trying to understand it. In fact, he was visiting my site and using infocard on it even before I had finished porting it. He actually stunned me – I thought there was some kind of an error since it never occured to me that someone would be using the system before I had even announced it was working!
Rohan tells it as he sees it, and this posting is no exception. First he shows a graphic that proves he has logged in, which is great. Then he notes that the current incarnation takes you to a dashboard where you see a link to browsehappy.com. He points out:
The first page of browsehappy.com has text that reads as : “Internet Explorer can make your computer unsafe. Why not switch to a browser that's more secure?”.
I read that and thought…. {{{nothing}}} I Know, I Know, browsehappy.com and wordpress are interlinked…
I have to smile. All of us will be attacked and all of us have to work hard – and together – to create a safe internet. So the kind of stuff on browsehappy doesn't even register with me – or, I suspect, with my long-tail subscribers.
Back on the subject at hand, Rohan continues:
I sent an infocard with Kim's own FirstName, LastName and email address (because from Kim's infocard invoker code, I saw that the only info he requested from an infocard was just the firstname, lastname and email address) and was able to login with that infocard too. However either with my own infocard or with a FAKE infocard with Kim's own info, I could not do much on the site. But the point is that regardless of the authenticity of the user, a “user” was provisioned on his blog.
Actually, the way the system works, you start off as a “subscription requestor”. You aren't recognized as a subscriber until you respond to an email sent to your email address.
When Rohan made his FAKE card and posed as me, I was the one who got the invitation to validate my email address. Clearly I didn't – it was obvious to me that someone was pulling my leg. When I've finished the implementation, it will also be impossible to socially engineer anyone into inadvertantly confirming an email. More about this later.
The email verification stage explains why, in the screen shot above, the bottom “cameron” subscription requestor is not shown as a subscriber. Over time, the fake registration attempt will time out and be deleted.
The net result is that the people who are promoted to subscriber can use their infocard to post comments on the site, wheras the fakes cannot.
None of this is yet implemented as well as it should be. I'm still experimenting.
But for people interested in trying things out, after you've logged in using an infocard and been approved through the mail validation, click on the “view site” portion of the dashboard. That takes you to the public identity blog. Then click on a “comment” link and leave a comment. It bypasses the moderation queue and gets posted immediately.
Using my subscriber InfoCard, for example, this is what I saw when I went to type in a comment:
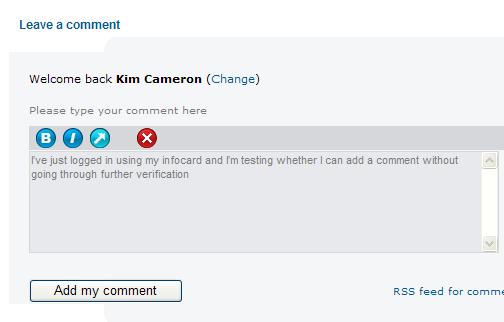
I pressed “Add my comment” and it was immediately posted.


Hi Kim,
An Attacker. thats a nice title, when the intention was not to “attack” but try to look at infocards from the other side. From another perspective altogether. Everybody seems to just nod heads when workflows and use case examples are explained. I have not seen many who have tried to disagree in the “open”.
Well, I am trying to do just that. Not disagree, but to look at it from another angle, and talk to you about my discoveries.
I'm sure that youd’ acknowledge, that I “did” inform you as soon as I logged into your site with FAKE info. Well, thats not called an “attack”.
As far as the “browsehappy.com” link goes, thats just a joke…
Like you said : All of us will be attacked and all of us have to work hard – and together – to create a safe internet. I AGREE with you. 100%. But lets be open to ideas that may be contradictory to our own….. My efforts are to create a SAFE internet. To point out issues and errors, so that one may work on fixing them.
Kim responds:
Rohan, I love you Rohan. I didn't mean “attacker” in the “normal” sense – I was talking about THE ROLE we refer to as security people, when we attempt, as you did, to think things through from the viewpoint of an attacker. I was actually delighted to have someone else in the community thinking through the possible attacks with me.
I meant what I said about you to be taken in a very positive sense. I appreciate what you are doing for exactly the reasons you express. I'll bring this up to the front page of the blog so no one misinterprets what I'm saying.
In terms of the browsehappy.com thing, I know it was a joke on your part! I was just talking about a couple of their claims, not about you.
So anyway, even though I sometimes write in a slightly sardonic way, please trust me to appreciate sincere and helpful contributions like yours.
Kim
I've just logged in using my infocard and I'm testting whether I can add a comment without going through further verification 🙂
I hope one day I will use My Personal smart USB key (processing My PSTS) to log on your blog.
More ‘test’ comments :-).
Be sure to look out for the verification e-mail that identityblog sends when using a self-signed card: on my system (which uses a very agressive filter) the e-mail was filtered as junk e-mail and so took me awhile to find. It'd be neat if verification systems could sign the verification email with a certificate that is related (visually) to the site presented in the Infocard ledger.