[This is the third installment of a presentation I gave to Microsoft developers at the Professional Developers Conference (PDC 2008) in Los Angeles. It starts here.]
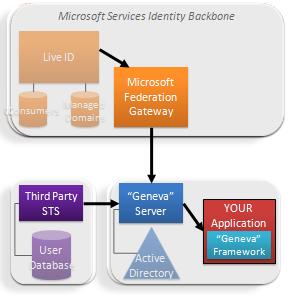
 Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID.
Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID.
It plays host to more than four hundred million consumer identities.
In the Geneva wave, Live ID will add “managed domain” services for sites and customers wanting to outsource their identity management. With this option, Live would take care of identity operations but the sign in/sign up UX can be customized to fit the look of your site.
But in what I think is an especially exciting evolution, Live IDs also get access to our cloud applications and developer services via the gateway, and are now part of the same open, standards-based architecture that underlies the rest of the Geneva Wave.
Microsoft Services Connector
Some customers may want to take advantage of Microsoft’s cloud applications, hosting, and developer services – and have Active Directory – but not be ready to start federating with others.
 We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway.
We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway.
This server is called the Microsoft Services Connector (MSC). It was built on Project Geneva technology.
Since it’s optimized for accessing Microsoft cloud applications it manages a single trust relationship with the Federation Gateway. Thus most of the configuration is fully automated. We think the Microsoft Services Connector will allow many enterprises to start working with federation in order to get access to our cloud, and that once they see the benefits, they’ll want to upgrade their functionality to embrace full federation through Geneva Server and multilateral federation.
Through the combination of Geneva Framework and Server, Microsoft Services Connector, Live ID, the Microsoft Federation Gateway – and the ability to use CardSpace to protect credentials on the Internet -millions of Live and AD users will have easy, secure, SSO access to our cloud applications and developer services.
But what about YOUR applications?

Well, since the Federation Gateway uses standard protocols and follows the claims-based model, if you write your application using a framework like “Geneva”, you can just plug it into the architecture and benefit from secure, SSO access by vast numbers of users – ALL the same users we do. The options open to us are open to you.
This underlines my conviction that Microsoft has really stepped up to the plate in terms of federation. We haven't simply made it easier for you to federate with US in order to consume OUR services. We are trying to make you as successful as we can in this amazing new era of identity. The walled garden is down. We want to move forward with developers in a world not constrained by zero sum thinking.
Configure your application to accept claims from the Microsoft Federation Gateway and you can receive claims from Live ID and any of the enterprise and government Federation Gateway partners who want to subscribe to your service. Or ignore the MFG and connect directly to other enterprises and other gateways that might emerge. Or connect to all of us.
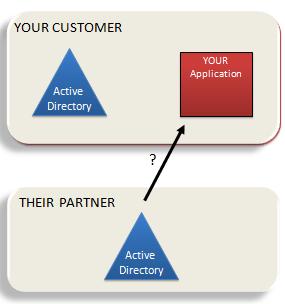
Crossing organizational boundaries
If this approach sounds too good to be true, some of you may wonder whether, to benefit from Microsoft's identity infrastructure, you need to jump onto our cloud and be trapped there even if you don't like it!
But the claims-based model moves completely beyond any kind of identity lock-in. You can run your application whereever you want – on your customer's premise, in some other hosting environment, even in your garage. You just configure it to point to the Microsoft Federation Gateway – or any other STS – as a source of claims.
 These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm.
These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm.
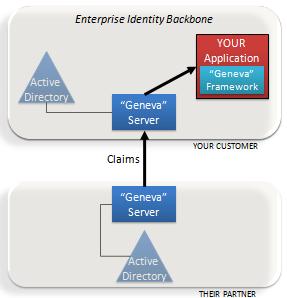
Do you want choice or more choice?
For even more flexibility, you can use an enterprise-installed “Geneva” server as your application's claim source, and configure that server to accept claims from a number of gateways and direct partners.
In the configuration shown here, the Geneva server can accept claims both hundreds of millions of Live ID users and from a partner who federates directly.
Claims-based access really does mean applications are written once, hosted anywhere. Identity source is a choice, not a limitation.
You get the ability to move in and out of the cloud at any time and for any reason.
Even more combinations are possible and are just a function of application configuration. It’s a case of “Where do you want to get claims today?”. And the answer is that you are in control.
In the next installment of this presentation I'll tell you about another service we are announcing – again a claims-based service but this time focussing on authorization. I'll also link to the demo, by Vittorio Bertocci, of how all these things fit together.

 The “Geneva” Framework: A framework you use in your .Net application for handling claims. This was formerly called “Zermatt”.
The “Geneva” Framework: A framework you use in your .Net application for handling claims. This was formerly called “Zermatt”.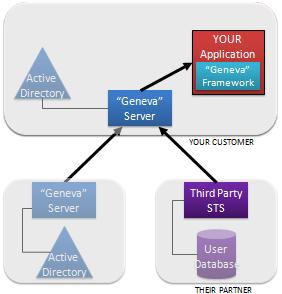 Anyone who has been around the block a few times knows there is one fatal flaw in the solution I’ve just described.
Anyone who has been around the block a few times knows there is one fatal flaw in the solution I’ve just described. I’m here today to tell you Microsoft has fully stepped up to the plate around federation. And it is already providing a lot of benefits and solving problems.
I’m here today to tell you Microsoft has fully stepped up to the plate around federation. And it is already providing a lot of benefits and solving problems.