[This is the fifth – and thankfully the final – installment of a presentation I gave to Microsoft developers at the Professional Developers Conference (PDC 2008) in Los Angeles. It starts here.]
I've made a number of announcements today that I think will have broad industry-wide support not only because they are cool, but because they indelibly mark Microsoft's practical and profound committment to an interoperable identity metasystem that reaches across devices, platforms, vendors, applications, and administrative boundaries.
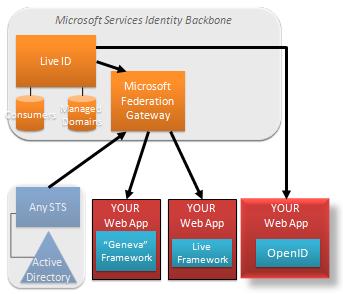
I'm very happy, in this context, to announce that from now on, all Live ID's will also work as OpenIDs.
That means the users of 400 million Live ID accounts will be able to log in to a large number of sites across the internet without a further proliferation of passwords – an important step forward for binging reduced password fatigue to the long tail of small sites engaged in social networking, blogging and consumer services.
As the beta progresses, CardSpace will be integrated into the same offering (there is already a separate CardSpace beta for Live ID).
Again, we are stressing choice of protocol and framework.
Beyond this support for a super lightweight open standard, we have a framework specifically tailored for those who want a very lightweight way to integrate tightly with a wider range of Live capabilities.
The Live Framework gives you access to an efficient, lightweight protocol that we use to optimize exchanges within the Live cloud.
It too integrates with our Gateway. Developers can download sample code (available in 7 languages), insert it directly into their application, and get access to all the identities that use the gateway including Live IDs and federated business users connecting via Geneva, the Microsoft Services Connector, and third party Apps.
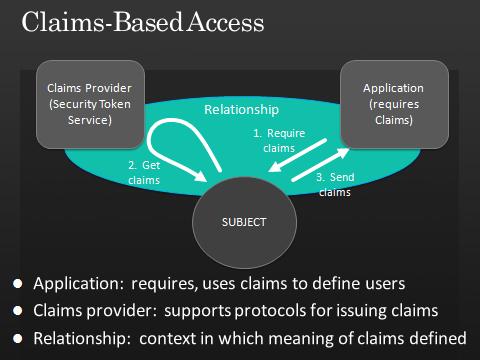
Flexible and Granular Trust Policy
Decisions about access control and personalization need to be made by the people responsible for resources and information – including personal information. That includes deciding who to trust – and for what.
At Microsoft, our Live Services all use and trust the Microsoft Federation Gateway, and this is helpful in terms of establishing common management, quality control, and a security bar that all services must meet.
But the claims-based model also fully supports the flexible and granular trust policies needed in very specialized contexts. We already see some examples of this within our own backbone.
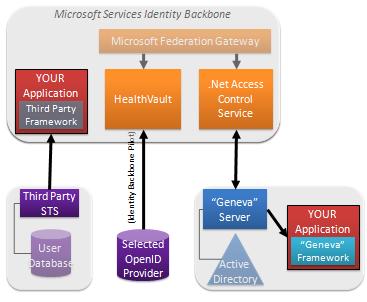
For example, we’ve been careful to make sure you can use Azure to build a cloud application – and yet get claims directly from a third party STS using a different third party’s identity framework, or directly from OpenID providers. Developers who take this approach never come into contact with our backbone.
Our Azure Access Control Service provides another interesting example. It is, in fact, a security component that can be used to provide claims about authorization decisions. Someone who wants to use the service might want their application, or its STS, to consume ACS directly, and not get involved with the rest of our backbone. We understand that. Trust starts with the application and we respect that.
Still another interesting case is HealthVault. HealthVault decided from day one to accept OpenIDs from a set of OpenID providers who operate the kind of robust claims provider needed by a service handling sensitive information. Their requirement has given us concrete experience, and let us learn about what it means in practice to accept claims via OpenID. We think of it as pilot, really, from which we can decide how to evolve the rest of our backbone.
So in general we see our Identity Backbone and our federation gateway as a great simplifying and synergizing factor for our Cloud services. But we always put the needs of trustworthy computing first and foremost, and are able to be flexible because we have a single identity model that is immune to deployment details.
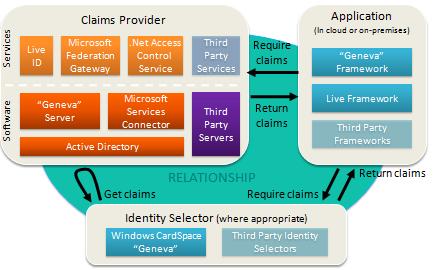
Identity Software + Services
To transition to the services world, the identity platform must consist of both software components and services components.
We believe Microsoft is well positioned to help developers in this critical area.
Above all, to benefit from the claims-based model, none of these components is mandatory. You select what is appropriate.
We think the needs of the application drive everything. The application specifies the claims required, and the identity metasystem needs to be flexible enough to supply them.
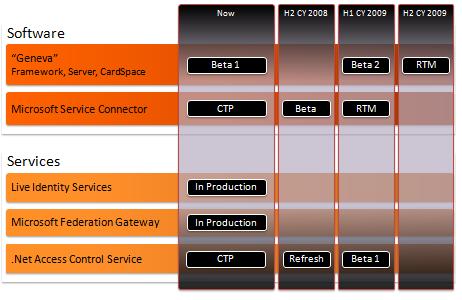
Roadmap
Our roadmap looks like this:
Identity @ PDC
You can learn more about every component I mentioned today by drilling into the 7 other presentations presented at PDC (watch the videos…):
Software
(BB42) Identity: “Geneva” Server and Framework Overview
(BB43) Identity: “Geneva” Deep Dive
(BB44) Identity: Windows CardSpace “Geneva” Under the Hood
Services
(BB22) Identity: Live Identity Services Drilldown
(BB29) Identity: Connecting Active Directory to Microsoft Services
(BB28) .NET Services: Access Control Service Drilldown
(BB55) .NET Services: Access Control In the Cloud Services
Conclusion
I once went to a hypnotist to help me give up smoking. Unfortunately, his cure wasn’t very immediate. I was able to stop – but it was a decade after my session.
Regardless, he had one trick I quite liked. I’m going to try it out on you to see if I can help focus your take-aways from this session. Here goes:
I’m going to stop speaking, and you are going to forget about all the permutations and combinations of technology I took you through today. You’ll remember how to use the claims based model. You’ll remember that we’ve announced a bunch of very cool components and services. And above all, you will remember just how easy it now is to write applications that benefit from identity, through a single model that handles every identity use case, is based on standards, and puts users in control.

 Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID.
Microsoft also operates one of the largest Claims Providers in the world – our cloud identity provider service, Windows Live ID. We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway.
We want to make it very easy for people to use our cloud applications and developer services without having to make any architectural decisions. So for that audience, we have built a fixed function server to federate Active Directory directly to the Microsoft Federation Gateway. OK. This is all very nice for Microsoft's apps, but how do other application developers benefit?
OK. This is all very nice for Microsoft's apps, but how do other application developers benefit?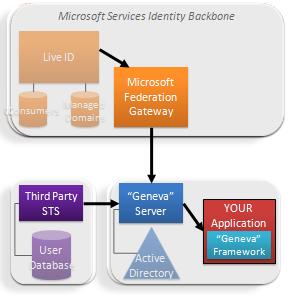 These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm.
These benefits are a great demonstration of how well the claims model spans organizational boundaries. We really do move into a “write once and run anywhere” paradigm. 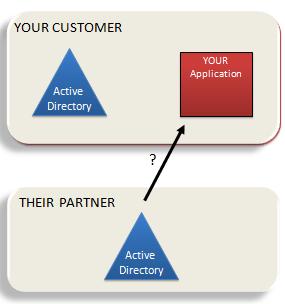
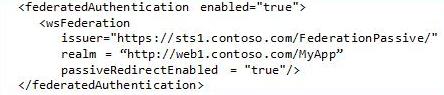
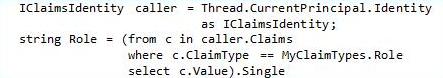
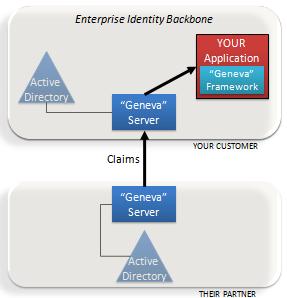 The “Geneva” Framework: A framework you use in your .Net application for handling claims. This was formerly called “Zermatt”.
The “Geneva” Framework: A framework you use in your .Net application for handling claims. This was formerly called “Zermatt”.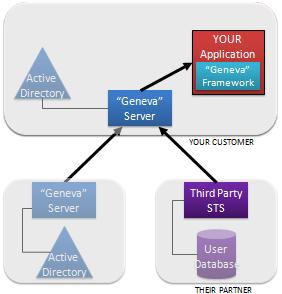 Anyone who has been around the block a few times knows there is one fatal flaw in the solution I’ve just described.
Anyone who has been around the block a few times knows there is one fatal flaw in the solution I’ve just described. I’m here today to tell you Microsoft has fully stepped up to the plate around federation. And it is already providing a lot of benefits and solving problems.
I’m here today to tell you Microsoft has fully stepped up to the plate around federation. And it is already providing a lot of benefits and solving problems. Whether you are creating serious Internet banking systems, hip new social applications, multi-party games or business applications for enterprise and government, you need to know something about the person using your application. We call this identity.
Whether you are creating serious Internet banking systems, hip new social applications, multi-party games or business applications for enterprise and government, you need to know something about the person using your application. We call this identity.