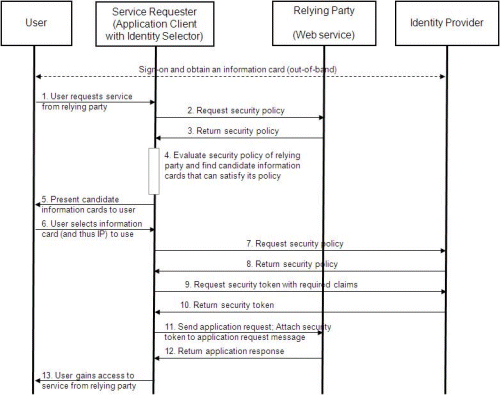
Network World's John Fontana has done a great job of explaining what it means for Microsoft to integrate U-Prove into its offerings:
Microsoft plans to incorporate U-Prove into both Windows Communication Foundation (WCF) and CardSpace, the user-centric identity software in Vista and XP.
Microsoft said all its servers and partner products that incorporate the WCF framework would provide support for U-Prove.
“The main point is that this will just become part of the base identity infrastructure we offer. Good privacy practices will become one of the norms of e-commerce,” Cameron said.
“The U-Prove technology looks like a good candidate as an authentication mechanism for CardSpace-managed cards (i.e., those cards issued by an identity provider),” Mark Diodati, an analyst with the Burton Group, wrote on his blog.
In general, the technology ensures that users always have say over what information they release and that the data can not be linked together by the recipients. That means that recipients along the chain of disclosure can not aggregate the data they collect and piece together the user’s personal information.
Eric Norlin has this piece in CSO, and Nancy Gohring's ComputerWorld article emphasizes that “U-Prove is the equivalent in the privacy world of RSA in the security space.” Burton's Mark Diodati covers the acquisition here.
Gunnar Peterson from 1 Raindrop notes in That Was Fast:
…the digital natives may be getting some better tooling faster than I thought. I am sure you already know there is a northern alliance and Redmond is U-Prove enabled. I fondly remember a lengthy conversation I had with Stefan Brands in Croatia several years ago, while he patiently explained to me how misguided the security-privacy collision course way of thinking is, and instead how real security is only achieved with privacy. If you have not already, I recommend you read Stefans’ primer on user identification.
Entrepreneur and angel investor Austin Hill gives us some background and links here:
In the year 2000, Zero-Knowledge acquired the rights to Dr. Stefan Brands work and hired Stefan to help us build privacy-enhanced identity & payments systems. It turns out we were very early into the identity game, failed to commercialize the technology – and during the Dot.Com bust cycle we shut down the business unit and released the patents back to Stefan. This was groundbreaking stuff that Stefan had invented, and we invested heavily in trying to make it real, but there weren’t enough bitters in the market at that time. We referred to the technologies as the “RSA” algorithms of the identity & privacy industry. Unfortunately the ‘privacy & identity’ industry didn’t exist.
Stefan went on to found Crendentica to continue the work of commercialization of his invention. Today he announced that Microsoft has acquired his company and he and his team are joining Microsoft.
Microsoft’s Identity Architect Guru Kim Cameron has more on the deal on his blog (he mentions the RSA for privacy concept as well).
Adam Shostack (former Zero Knowledge Evil Genius, who also created a startup & currently works at Microsoft) has this post up. George Favvas, CEO of SmartHippo (also another Zero-Knowledge/Total.Net alumni – entrepreneur) also blogged about the deal as well.
Congratulations to Stefan and the team. This is a great deal for Microsoft, the identity industry and his team. (I know we tried to get Microsoft to buy or adopt the technology back in 2001 🙂
(I didn't really know much about Zero-Knowledge back in 2000, but it's interesting to see how early they characterized of Stefan's technology as being the privacy equivalent of RSA. It's wonderful to see people who are so forward-thinking.)
Analyst Neil Macehiter writes:
Credentica was founded by acknowledged security expert Stefan Brands, whose team has applied some very advanced cryptography techniques to allow users to authenticate to service providers directly without the involvement of identity providers. They also limit the disclosure of personally-identifiable information to prevent accounts being linked across service providers and provide resistance to phishing attacks. Credentica's own marketing literature highlights the synergies with CardSpace:
“`The SDK is ideally suited for creating the electronic equivalent of the cards in one's wallet and for protecting identity-related information in frameworks such as SAML, Liberty ID-WSF, and Windows CardSpace.”
This is a smart move by Microsoft. Not only does it bring some very innovative and well-respected technology (with endorsements from the likes of the Information and Privacy Commissioner of Ontario, Canada) which extends the capabilities of Microsoft's identity and security offerings; it also brings some heavyweight cryptography and privacy expertise and credibility from the Credentica team. The latter can, and undoubtedly will, be exploited by Microsoft in the short term: the former will take more time to realise with Microsoft stating that integrated offerings are at least 12–18 months away.
Besides the many positives, there were concerns expressed about whether Microsoft would make the technology available beyond Windows. Ben Laurie wrote:
Kim and Stefan blog about Microsoft’s acquisition of Stefan’s selective disclosure patents and technologies, which I’ve blogged about many times before.
This is potentially great news, especially if one interprets Kim’s
Our goal is that Minimal Disclosure Tokens will become base features of identity platforms and products, leading to the safest possible intenet. I don’t think the point here is ultimately to make a dollar. It’s about building a system of identity that can withstand the ravages that the Internet will unleash.
in the most positive way. Unfortunately, comments such as this from Stefan
Microsoft plans to integrate the technology into Windows Communication Foundation and Windows Cardspace.
and this from Microsoft’s Privacy folk
When this technology is broadly available in Microsoft products (such as Windows Communication Foundation and Windows Cardspace), enterprises, governments, and consumers all stand to benefit from the enhanced security and privacy that it will enable.
sound more like the Microsoft we know and love.
I hope everyone who reads this blog knows that it is elementary, my dear Laurie, that identity technology must work across boundaries, platforms and vendors (Law 5 – not to mention, “Since the identity system has to work on all platforms, it must be safe on all platforms”).
That doesn't mean it is trivial to figure out the best legal mecahnisms for making the intellectual property and even the code available to the ecosystem. Lawyers are needed, and it takes a while. But I can guarantee everyone that I have zero intention of hoarding Minimal Disclosure Tokens or turning U-Prove into a proprietary Microsoft technology silo.
Like, it's 2008, right? Give me a break, guys!